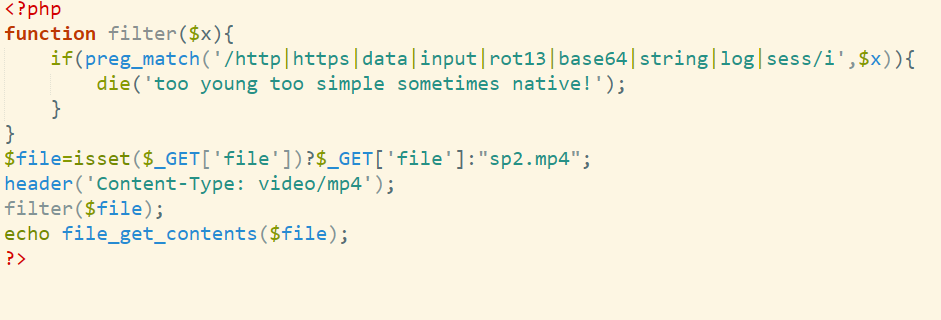
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
| import time
opc = [0x00000000, 0x00000001, 0x00000200, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000004, 0x00000002, 0x00000001, 0x00000004, 0x00000005, 0x00000003, 0x00000004, 0x00000005,
0x00000050, 0x00000002, 0x00000003, 0x00000000, 0x00000004, 0x00000008, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFE4, 0x00000000, 0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFE4,
0x00000004, 0x00000004, 0x00000002, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFD8, 0x00000002, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0xFFFFFFE4, 0x00000002, 0x00000006,
0x00000000, 0x00000003, 0x00000000, 0x00000002, 0x00000005, 0x00000004, 0xFFFFFFFF, 0x00000000, 0x00000004, 0x00000002, 0x00000004, 0xFFFFFFE4, 0x00000001, 0x00000009, 0x00000002, 0x00000004,
0xFFFFFFFF, 0x00000000, 0x0000000A, 0x00000029, 0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFE4, 0x00000003, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFD8, 0x00000002, 0x00000000,
0x00000004, 0xFFFFFFD4, 0x00000002, 0x00000009, 0x00000002, 0x00000004, 0xFFFFFFD4, 0x00000020, 0x0000000F, 0x0000005B, 0x00000011, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0x00000008,
0x00000002, 0x00000000, 0x00000004, 0xFFFFFFE0, 0x00000003, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFB0, 0x00000053, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFB1, 0x00000068, 0x00000002,
0x00000002, 0x00000004, 0xFFFFFFB2, 0x0000006F, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFB3, 0x00000077, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFB4, 0x0000006D, 0x00000002, 0x00000002,
0x00000004, 0xFFFFFFB5, 0x00000061, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFB6, 0x0000006B, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFB7, 0x00000065, 0x00000002, 0x00000002, 0x00000004,
0xFFFFFFB8, 0x00000072, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFB9, 0x0000005F, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFBA, 0x0000006D, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFBB,
0x00000061, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFBC, 0x00000064, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFBD, 0x00000065, 0x00000002, 0x00000002, 0x00000004, 0xFFFFFFBE, 0x00000069,
0x00000002, 0x00000002, 0x00000004, 0xFFFFFFBF, 0x00000074, 0x00000006, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFB0, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFF4, 0x00000000, 0x00000002,
0x00000007, 0x00000004, 0xFFFFFFD0, 0xA0A01919, 0x00000002, 0x00000004, 0x00000002, 0x00000004, 0x00000012, 0x00000004, 0x00000003, 0x00000002, 0x00000000, 0x00000002, 0x00000003, 0x00000000,
0x00000004, 0xFFFFFFF4, 0x00000002, 0x00000008, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFCC, 0x00000002, 0x00000002, 0x00000004, 0x00000003, 0x00000004,
0x00000008, 0x00000004, 0x00000003, 0x00000000, 0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFF4, 0x00000002, 0x00000008, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000000,
0x00000004, 0xFFFFFFC8, 0x00000002, 0x00000002, 0x00000004, 0x00000003, 0x00000004, 0x00000008, 0x00000004, 0x00000003, 0x00000001, 0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFF4,
0x00000002, 0x00000008, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFC4, 0x00000002, 0x00000002, 0x00000004, 0x00000003, 0x00000004, 0x00000012, 0x00000004,
0x00000000, 0x00000003, 0x00000003, 0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFF4, 0x00000002, 0x00000008, 0x00000003, 0x00000002, 0x00000000, 0x00000002, 0x00000000, 0x00000004,
0xFFFFFFC0, 0x00000003, 0x00000002, 0x00000007, 0x00000004, 0xFFFFFFF8, 0x00000000, 0x0000000C, 0x00000137, 0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFF8, 0x00000004, 0x00000004,
0x00000000, 0x00000002, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFF8, 0x00000000, 0x00000009, 0x00000002, 0x00000004, 0xFFFFFFF8, 0x00000008, 0x00000013, 0x00000268, 0x00000002, 0x00000003,
0x00000002, 0x00000004, 0xFFFFFFF8, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0xFFFFFFE0, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000002, 0x00000004, 0x00000002, 0x00000000,
0x00000004, 0xFFFFFFEC, 0x00000000, 0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFF8, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0xFFFFFFE0, 0x00000002, 0x0000000A, 0x00000000,
0x00000003, 0x00000002, 0x00000004, 0x00000004, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFE8, 0x00000000, 0x00000002, 0x00000007, 0x00000004, 0xFFFFFFF0, 0x00000000, 0x00000002, 0x00000007,
0x00000004, 0xFFFFFFDC, 0x00000000, 0x0000000C, 0x00000183, 0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFDC, 0x00000004, 0x00000004, 0x00000002, 0x00000001, 0x00000002, 0x00000000,
0x00000004, 0xFFFFFFDC, 0x00000002, 0x00000009, 0x00000002, 0x00000004, 0xFFFFFFDC, 0x00000048, 0x00000014, 0x0000023B, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0xFFFFFFE8, 0x00000007,
0x00000004, 0x00000003, 0x00000005, 0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFE8, 0x00000008, 0x00000004, 0x00000000, 0x00000006, 0x00000005, 0x00000001, 0x00000003, 0x00000000,
0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFE8, 0x00000005, 0x00000004, 0x00000002, 0x11223344, 0x00000004, 0x00000001, 0x00000003, 0x00000002, 0x00000002, 0x00000003, 0x00000002,
0x00000004, 0xFFFFFFF0, 0x0000000D, 0x00000004, 0x00000002, 0x00000003, 0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFF4, 0x00000002, 0x00000009, 0x00000002, 0x00000000, 0x00000002,
0x00000004, 0x00000004, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFF0, 0x00000005, 0x00000004, 0x00000002, 0xABAB1212, 0x00000005, 0x00000001, 0x00000003, 0x00000002, 0x00000004, 0x00000003,
0x00000003, 0x00000004, 0xFFFFFFEC, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFEC, 0x00000003, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0xFFFFFFF0, 0x00000003, 0x00000003, 0x00000003,
0x00000004, 0xFFFFFFD0, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFF0, 0x00000003, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0xFFFFFFEC, 0x00000007, 0x00000004, 0x00000003, 0x00000004,
0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFEC, 0x00000008, 0x00000004, 0x00000000, 0x00000007, 0x00000005, 0x00000001, 0x00000003, 0x00000000, 0x00000002, 0x00000003, 0x00000002,
0x00000004, 0xFFFFFFEC, 0x00000005, 0x00000004, 0x00000002, 0x55667788, 0x00000004, 0x00000001, 0x00000003, 0x00000002, 0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFF0, 0x00000007,
0x00000004, 0x00000000, 0x0000000B, 0x0000000D, 0x00000004, 0x00000000, 0x00000003, 0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFF4, 0x00000002, 0x00000009, 0x00000000, 0x00000002,
0x00000000, 0x00000004, 0x00000004, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFF0, 0x00000005, 0x00000004, 0x00000000, 0x23235566, 0x00000005, 0x00000001, 0x00000000, 0x00000003, 0x00000004,
0x00000003, 0x00000000, 0x00000004, 0xFFFFFFE8, 0x00000002, 0x00000000, 0x00000004, 0xFFFFFFE8, 0x00000000, 0x0000000C, 0x00000175, 0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFF8,
0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFE0, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0xFFFFFFEC, 0x00000002, 0x0000000B, 0x00000002, 0x00000000, 0x00000004, 0x00000003,
0x00000002, 0x00000003, 0x00000000, 0x00000004, 0xFFFFFFF8, 0x00000002, 0x00000003, 0x00000002, 0x00000004, 0xFFFFFFE0, 0x00000002, 0x00000003, 0x00000003, 0x00000004, 0xFFFFFFE8, 0x00000002,
0x0000000C, 0x00000002, 0x00000000, 0x00000004, 0x00000004, 0x00000003, 0x0000000C, 0x00000129, 0x00000002, 0x00000001, 0x00000005, 0x00000004, 0x00000001, 0x00000000, 0x00000000, 0x00000000]
reg = [0x0] * 11
memory = [0x0] * 144
memory[128] = 0x30303030
memory[129] = 0x31313131
memory[130] = 0x31313131
memory[131] = 0x31313131
memory[132] = 0x32323232
memory[133] = 0x32323232
memory[134] = 0x33333333
memory[135] = 0x33333333
reg[4] = 0
reg[5] = 0x100
result = []
while reg[6] < len(opc):
if opc[reg[6]] == 0:
index = (reg[5]-4)//4
reg[5] -= 4
if opc[reg[6]+1] == 0:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, asm: mov memory[{index}], reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}")
memory[index] = reg[opc[reg[6]+2]]
elif opc[reg[6]+1] == 1:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, asm: mov memory[{index}], {hex(opc[reg[6]+2])}")
memory[index] = opc[reg[6]+2]
reg[6] += 3
elif opc[reg[6]] == 1:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, asm: end of VM")
for j in range(128, 136):
result.append(memory[j])
reg[6] += 2
break
elif opc[reg[6]] == 2:
if opc[reg[6]+1] == 0:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: mov memory[{((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4])}, reg[{opc[reg[6]+4]}] = {hex(reg[opc[reg[6]+4]])}")
memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = reg[opc[reg[6]+4]]
reg[6] += 5
elif opc[reg[6]+1] == 1:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: mov reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, reg[{opc[reg[6]+3]}] = {hex(reg[opc[reg[6]+3]])}")
reg[opc[reg[6]+2]] = reg[opc[reg[6]+3]]
reg[6] += 4
elif opc[reg[6]+1] == 2:
BYTEPlace = ((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)%4
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: mov ({BYTEPlace}#BYTE)memory[{((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4}] = {hex((memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&(0xFF<<(BYTEPlace*8)))>>BYTEPlace*8)}, reg[{opc[reg[6]+4]}] = {hex(opc[reg[6]+4])}")
if BYTEPlace == 0: memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = (memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&0xFFFFFF00)|((opc[reg[6]+4]&0xFF)<<(8*BYTEPlace))
elif BYTEPlace == 1: memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = (memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&0xFFFF00FF)|((opc[reg[6]+4]&0xFF)<<(8*BYTEPlace))
elif BYTEPlace == 2: memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = (memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&0xFF00FFFF)|((opc[reg[6]+4]&0xFF)<<(8*BYTEPlace))
elif BYTEPlace == 3: memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = (memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&0x00FFFFFF)|((opc[reg[6]+4]&0xFF)<<(8*BYTEPlace))
reg[6] += 5
elif opc[reg[6]+1] == 3:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: mov reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4]
reg[6] += 5
elif opc[reg[6]+1] == 4:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: mov reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, {hex(opc[reg[6]+3])}")
reg[opc[reg[6]+2]] = opc[reg[6]+3]
reg[6] += 4
elif opc[reg[6]+1] == 5:
BYTEPlace = ((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)%4
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: mov ({BYTEPlace}#BYTE)memory[{((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4}] = {hex((memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&(0xFF<<(BYTEPlace*8)))>>BYTEPlace*8)}, (BYTE)reg[{opc[reg[6]+4]}] = {hex(reg[opc[reg[6]+4]]&0xFF)}")
if BYTEPlace == 0: memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = ((memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4])&0xFFFFFF00)+((reg[opc[reg[6]+4]]*0x00000001)&0x000000FF)
elif BYTEPlace == 1: memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = ((memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4])&0xFFFF00FF)+((reg[opc[reg[6]+4]]*0x00000100)&0x0000FF00)
elif BYTEPlace == 2: memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = ((memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4])&0xFF00FFFF)+((reg[opc[reg[6]+4]]*0x00010000)&0x00FF0000)
elif BYTEPlace == 3: memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = ((memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4])&0x00FFFFFF)+((reg[opc[reg[6]+4]]*0x01000000)&0xFF000000)
reg[6] += 5
elif opc[reg[6]+1] == 6:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: mov (LOBYTE)reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]]&0xFF)}, ({((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)%4}#BYTE)memory[{((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4}] = {hex(((memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4]>>((((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)%4)*8))&0xFF))}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+2]]&0xFFFFFF00)+((memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4]>>((((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)%4)*8))&0xFF)
reg[6] += 5
elif opc[reg[6]+1] == 7:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: mov memory[{((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4])}, {hex(opc[reg[6]+4])}")
memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = opc[reg[6]+4]
reg[6] += 5
elif opc[reg[6]+1] == 8:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: mov reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = memory[((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]])&0xFFFFFFFF)//4]
reg[6] += 5
elif opc[reg[6]+1] == 9:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, {hex(opc[reg[6]+5])}, asm: mov reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]]*opc[reg[6]+5])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]]*opc[reg[6]+5])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = memory[((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]]*opc[reg[6]+5])&0xFFFFFFFF)//4]
reg[6] += 6
elif opc[reg[6]+1] == 10:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, {hex(opc[reg[6]+5])}, {hex(opc[reg[6]+6])}, asm: mov reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]]*opc[reg[6]+5]+opc[reg[6]+6])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]]*opc[reg[6]+5]+opc[reg[6]+6])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = memory[((reg[opc[reg[6]+3]]+reg[opc[reg[6]+4]]*opc[reg[6]+5]+opc[reg[6]+6])&0xFFFFFFFF)//4]
reg[6] += 7
elif opc[reg[6]+1] == 11:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, {hex(opc[reg[6]+5])}, asm: mov memory[{((reg[opc[reg[6]+2]]+reg[opc[reg[6]+3]*opc[reg[6]+4]])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+2]]+reg[opc[reg[6]+3]*opc[reg[6]+4]])&0xFFFFFFFF)//4])}, reg[{opc[reg[6]+5]}] = {hex(reg[opc[reg[6]+5]])}")
memory[((reg[opc[reg[6]+2]]+reg[opc[reg[6]+3]]*opc[reg[6]+4])&0xFFFFFFFF)//4] = reg[opc[reg[6]+5]]
reg[6] += 6
elif opc[reg[6]+1] == 12:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, {hex(opc[reg[6]+5])}, {hex(opc[reg[6]+6])}, asm: mov memory[{((reg[opc[reg[6]+2]]+reg[opc[reg[6]+3]]*opc[reg[6]+4]+opc[reg[6]+5])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+2]]+reg[opc[reg[6]+3]]*opc[reg[6]+4]+opc[reg[6]+5])&0xFFFFFFFF)//4])}, reg[{opc[reg[6]+6]}] = {hex(reg[opc[reg[6]+6]])}")
memory[((reg[opc[reg[6]+2]]+reg[opc[reg[6]+3]]*opc[reg[6]+4]+opc[reg[6]+5])&0xFFFFFFFF)//4] = reg[opc[reg[6]+6]]
reg[6] += 7
elif opc[reg[6]] == 3:
if opc[reg[6]+1] == 3:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: sub reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+2]]-memory[(
(reg[opc[reg[6]+3]]+opc[reg[6]+4]) & 0xFFFFFFFF)//4]) & 0xFFFFFFFF
reg[6] += 5
elif opc[reg[6]+1] == 4:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: sub reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, {hex(opc[reg[6]+3])}")
reg[opc[reg[6]+2]] -= opc[reg[6]+3]
reg[6] += 4
elif opc[reg[6]] == 4:
if opc[reg[6]+1] == 1:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: add reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, {hex(reg[opc[reg[6]+3]])}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+2]]+reg[opc[reg[6]+3]])&0xFFFFFFFF
reg[6] += 4
elif opc[reg[6]+1] == 2:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: add memory[{((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4])}, {hex(opc[reg[6]+4])}")
memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4] = (memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]+opc[reg[6]+4])&0xFFFFFFFF
reg[6] += 5
elif opc[reg[6]+1] == 3:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: add reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+2]]+memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4])&0xFFFFFFFF
reg[6] += 5
elif opc[reg[6]+1] == 4:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: add reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, {hex(opc[reg[6]+3])}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF
reg[6] += 4
elif opc[reg[6]] == 5:
if opc[reg[6]+1] == 1:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: xor reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, reg[{opc[reg[6]+3]}] = {hex(reg[opc[reg[6]+3]])}")
reg[opc[reg[6]+2]] = reg[opc[reg[6]+2]] ^ reg[opc[reg[6]+3]]
reg[6] += 4
elif opc[reg[6]+1] == 2:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: xor memory[reg[arg2]+arg3], arg4")
reg[6] += 5
elif opc[reg[6]+1] == 3:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: xor arg2, memory[reg[arg3]+arg4]")
reg[6] += 5
elif opc[reg[6]+1] == 4:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: xor reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, {hex(opc[reg[6]+3])}")
reg[opc[reg[6]+2]] = reg[opc[reg[6]+2]] ^ opc[reg[6]+3]
reg[6] += 4
elif opc[reg[6]] == 6:
assert opc[reg[6]+1] == 3
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: add reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, reg[{opc[reg[6]+3]}] = {hex(reg[opc[reg[6]+3]])}, {hex(opc[reg[6]+4])}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF
reg[6] += 5
elif opc[reg[6]] == 7:
if opc[reg[6]+1] == 3:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: shr reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = reg[opc[reg[6]+2]] >> memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4]
reg[6] += 5
elif opc[reg[6]+1] == 4:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: shr reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, {hex(opc[reg[6]+3])}")
reg[opc[reg[6]+2]] = reg[opc[reg[6]+2]] >> opc[reg[6]+3]
reg[6] += 4
elif opc[reg[6]] == 8:
if opc[reg[6]+1] == 3:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: shl reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+2]] << memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4])&0xFFFFFFFF
reg[6] += 5
elif opc[reg[6]+1] == 4:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: shl reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, {hex(opc[reg[6]+3])}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+2]] << opc[reg[6]+3])&0xFFFFFFFF
reg[6] += 4
elif opc[reg[6]] == 9:
BYTEPlace = ((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)%4
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: cmp (#{BYTEPlace}BYTE)memory[{((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4}] = {hex((memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&int('0xFF'+'00'*BYTEPlace,16))>>BYTEPlace*8)}, {hex(opc[reg[6]+4])}")
if (memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&(0xFF<<(BYTEPlace*8)))>>BYTEPlace*8 == opc[reg[6]+4]:
reg[7] = 1
reg[8] = reg[9] = reg[10] = 0
elif (memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&(0xFF<<(BYTEPlace*8)))>>BYTEPlace*8 > opc[reg[6]+4]:
reg[7] = reg[8] = reg[9] = reg[10] = 0
elif (memory[((reg[opc[reg[6]+2]]+opc[reg[6]+3])&0xFFFFFFFF)//4]&(0xFF<<(BYTEPlace*8)))>>BYTEPlace*8 < opc[reg[6]+4]:
reg[7] = reg[10] = 0
reg[8] = reg[9] = 1
reg[6] += 5
elif opc[reg[6]] == 10:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, asm: jz(xmm[0]) {hex(opc[reg[6]+1])}",end=" ")
if reg[7] == 0:
print("jumped here")
reg[6] = opc[reg[6]+1]
elif reg[7] == 1:
print("unjump here")
reg[6] += 2
elif opc[reg[6]] == 12:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, asm: jmp {hex(opc[reg[6]+1])}")
reg[6] = opc[reg[6]+1]
elif opc[reg[6]] == 13:
if opc[reg[6]+1] == 3:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, {hex(opc[reg[6]+4])}, asm: and reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, memory[{((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4}] = {hex(memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4])}")
reg[opc[reg[6]+2]] = reg[opc[reg[6]+2]] & memory[((reg[opc[reg[6]+3]]+opc[reg[6]+4])&0xFFFFFFFF)//4]
reg[6] += 5
elif opc[reg[6]+1] == 4:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: and reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, {hex(opc[reg[6]+3])}")
reg[opc[reg[6]+2]] = reg[opc[reg[6]+2]] & opc[reg[6]+3]
reg[6] += 4
elif opc[reg[6]] == 15:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, asm: jnz {hex(opc[reg[6]+1])}",end=" ")
if reg[7] == 1:
print("jumped here")
reg[6] = opc[reg[6]+1]
elif reg[7] == 0:
print("unjump here")
reg[6] += 2
elif opc[reg[6]] == 16:
print("op {reg[6]}: {hex(opc[reg[6]])}, asm: nop")
reg[6] += 1
elif opc[reg[6]] == 17:
print("Length Wrong!")
exit(0)
elif opc[reg[6]] == 18:
assert opc[reg[6]+1] == 4
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, {hex(opc[reg[6]+2])}, {hex(opc[reg[6]+3])}, asm: mul reg[{opc[reg[6]+2]}] = {hex(reg[opc[reg[6]+2]])}, reg[{opc[reg[6]+3]}] = {hex(reg[opc[reg[6]+3]])}, {hex(opc[reg[6]+4])}")
reg[opc[reg[6]+2]] = (reg[opc[reg[6]+3]]*opc[reg[6]+4])&0xFFFFFFFF
reg[6] += 5
elif opc[reg[6]] == 19:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, asm: je(xmm[1],xmm[3]) {hex(opc[reg[6]+1])}",end=" ")
if reg[8] == reg[10]:
print("jumped here")
reg[6] = opc[reg[6]+1]
else:
print("unjump here")
reg[6] += 2
elif opc[reg[6]] == 20:
print(f"op {reg[6]}: {hex(opc[reg[6]])}, {hex(opc[reg[6]+1])}, asm: jz(xmm[2]) {hex(opc[reg[6]+1])}",end=" ")
if reg[9] == 0:
print("jumped here")
reg[6] = opc[reg[6]+1]
elif reg[9] == 1:
print("unjump here")
reg[6] += 2
else:
print("opcode unknown: ", opc[reg[6]])
break
print("memory:")
for i in range(len(memory)):
print(f'{memory[i]:#10x}', end=' ')
if (i%16 == 15):
print()
print("reg:")
for i in range(len(reg)):
print(f'{reg[i]:#10x}', end=" ")
print()
print("result:")
for i in range(len(result)):
print(f'{result[i]:#10x}', end=" ")
print()
def bytes_to_dwords_little_endian(byte_array):
return [int.from_bytes(byte_array[i:i+4], byteorder='little', signed=False) for i in range(0, len(byte_array), 4)]
def dwords_to_bytes_little_endian(dword_array):
byte_list = []
for dword in dword_array:
byte_list.extend(dword.to_bytes(4, byteorder='little'))
return byte_list
m1 = 0x30303030
m2 = 0x31313131
delta = 0xA0A01919
key = [0x776F6853, 0x656B616D, 0x616D5F72, 0x74696564]
ttl = 0
for i in range(0x48):
m1 = (m1 + ((((m2 >> 5) ^ (m2 << 6)) + (m2 ^ 0x11223344)) ^ ((key[ttl & 3] + ttl) ^ 0xABAB1212))) & 0xFFFFFFFF
ttl = (ttl - delta) & 0xFFFFFFFF
m2 = (m2 + ((((m1 >> 4) ^ (m1 << 7)) + (m1 ^ 0x55667788)) ^ ((key[(ttl >> 11) & 3] + ttl) ^ 0x23235566))) & 0xFFFFFFFF
print(hex(m1), hex(m2))
time.sleep(1)
encflag = [0x9a,0x2e,0x6c,0x69,0xe1,0xe8,0xad,0x76,0xa4,0x5c,0x7d,0xe6,0x38,0xbd,0x76,0x5c,
0x87,0x07,0xac,0xb7,0x65,0x0c,0xea,0xbf,0x10,0xff,0xc2,0x01,0x38,0xfd,0x16,0x6d]
dwordenc = bytes_to_dwords_little_endian(encflag)
result = []
for j in range(0,len(dwordenc)//2):
m1 = dwordenc[2*j]
m2 = dwordenc[2*j+1]
ttl = (0 - 0x48 * delta) & 0xFFFFFFFF
for j in range(0x48):
m2 = (m2 - ((((m1 >> 4) ^ (m1 << 7)) + (m1 ^ 0x55667788)) ^ ((key[(ttl >> 11) & 3] + ttl) ^ 0x23235566))) & 0xFFFFFFFF
ttl = (ttl + delta) & 0xFFFFFFFF
m1 = (m1 - ((((m2 >> 5) ^ (m2 << 6)) + (m2 ^ 0x11223344)) ^ ((key[ttl & 3] + ttl) ^ 0xABAB1212))) & 0xFFFFFFFF
result.append(m1)
result.append(m2)
flag = dwords_to_bytes_little_endian(result)
time.sleep(1)
strflag = ''.join([chr(i) for i in flag])
print(strflag)
|