SUSCTF 2025 wp
SUSCTF wp
那几道逆向不太想复现了
MISC
Questionnaire
问卷
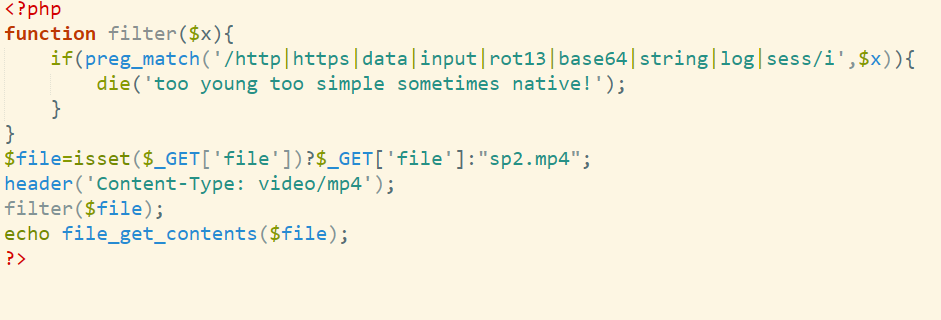
easyjail
AI直出
1 | import argparse |
curlbash
用了webhook和gist持久化一个文件链接
1 |
|
非预期出的
curlbash-revenge
1 | #!/bin/bash |
eat-mian
做一下替换然后去在线网站测试下就行
susctf{Mag1Cal_P7epr0ces$er_087604c6048d}
Crypto
03-CrySignin
GPT
04-Broadcast_1
AI出
1 | import socket, ast |
Web
am i admin?
AI出
1 | import requests |
am i admin?2
AI 出
1 | import requests |
RE
android-native
native里有RC4校验
key做了更改
1 | #!/usr/bin/env python3 |
susctf{de094624-8f5b-44dc-810c-58132a2b5ea3}
一个饼干人
Il2CppDumper 检测到“This file may be protected”——说明 so 有防护/修改,导致它选择不生成或生成失败对 IDA/Ghidra 的自动重命名脚本。
github上面的解释
Il2CppDumper检测到可执行文件已被保护,使用
GameGuardian从游戏内存中dumplibil2cpp.so,然后使用Il2CppDumper载入按提示操作,可绕过大部分保护
这里思路开始偏了,开始去用师傅的另一个项目去拿dump.cs
拿到之后,又偏了分析libcpp.so导入xx.h和xx.json这俩文件花了1个小时左右
最后发现逻辑无法分析,然后开始思考cookie
在asset下发现了delicous,查了下可以解包,用assetstudio没解出来
用的assetripper解出来了
手慢了大概没一会,本来二血,居然是小写的c….
SUSCTF{cookies_GOOD}
ezsignin
patch掉花指令,得到主逻辑,中间还有base58,rc4…
1 | alphabet = "123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz" |
susctf{Oh_My_G0d_You_@re_Rev3rse_God!!!}
made-in-haven
看到haven就想到了dubhectf做的一道天堂之门的题目…
看了下附件有很多retn和花指令混淆,都path掉再F5就可以得到主逻辑
先对key前8位和后8位做xor和sub
然后一个简单的TEA即可
1 | import base64, struct |
susctf{sp33d_up_time_t0_h34v3n!}