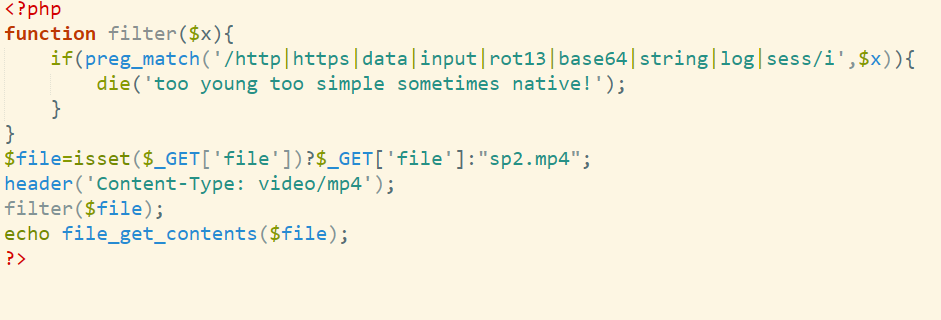
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
439
440
441
442
443
444
445
446
447
448
449
450
451
452
453
454
455
456
457
458
459
460
461
462
463
464
465
466
|
import random
from typing import List, Tuple
def func2(n: int) -> int:
a, b = 1, 1
for _ in range(n - 1):
a, b = b, a + b
return a
def func1(lss: List[str], i: int, j: int) -> int:
N = len(lss)
index = i * N + j
if arr[index] != -1:
return arr[index]
s1 = list(lss[i])
s2 = list(lss[j])
l1, l2 = len(s1), len(s2)
if l1 - l2 != 1:
arr[index] = 0
return 0
flag = True
n = 0
for m in range(l1):
if n < l2 and s1[m] == s2[n]:
n += 1
if n == l2:
break
else:
if flag:
flag = False
continue
else:
arr[index] = 0
return 0
arr[index] = 1
return 1
def abc(lss: List[str], i: int) -> int:
if abcarray[i] > 0:
return abcarray[i]
m = 1
for index, _word in enumerate(lss):
if func1(lss, i, index) == 1:
m = max(m, abc(lss, index) + 1)
abcarray[i] = m
return m
def solution(lss: List[str]) -> int:
global abcarray, arr
N = len(lss)
abcarray = [-1] * N
arr = [-1] * (N * N)
ans = 1
for i in range(N):
ans = max(ans, abc(lss, i))
return ans
def encode(s: str) -> List[int]:
ret: List[int] = []
ls = list(s)
if len(ls) % 2 != 0:
raise ValueError("encode函数要求字符串长度为偶数")
for i in range(0, len(ls), 2):
num1 = ord(ls[i])
num2 = ord(ls[i + 1])
numa = (num1 & 248) >> 3
numb = ((num1 & 7) << 3) | ((num2 & 240) >> 4)
numc = num2 & 15
ret += [numa, numb, numc]
return ret
def calc(nums: Tuple[int, int, int] or List[int]) -> str:
num1, num2, num3 = nums
num1 = 2023 + (num1 & 15) - (num1 & 240)
num2 = func2(num2 + 7)
random.seed(num3)
flag = f"{num1}{num2}{num3}{random.gauss(num2, 0.2)}"
flag = flag.replace(".", "x")
print("flag=", flag)
return flag
def decode_from_encode(nums: List[int]) -> str:
"""穷举 ASCII 字符,恢复两字符字符串"""
for c1 in range(32, 127):
for c2 in range(32, 127):
numa = (c1 & 248) >> 3
numb = ((c1 & 7) << 3) | ((c2 & 240) >> 4)
numc = c2 & 15
if [numa, numb, numc] == nums:
return chr(c1) + chr(c2)
raise ValueError(f"无法解码 encode {nums}")
def decode_from_encode_multi(nums: List[int]) -> str:
"""处理长度 >3 的 encode(两字符一组)"""
if len(nums) % 3 != 0:
raise ValueError("encode 数组长度必须是3的倍数")
s = ""
for i in range(0, len(nums), 3):
s += decode_from_encode(nums[i:i+3])
return s
if __name__ == "__main__":
str1 = "ba"
str2 = "ab"
str3 = "bc"
str4 = "cb"
str5 = "bdca"
str6 = "bacd"
str7 = "bbbb"
str8 = "acdb"
num1 = solution(
['a', str1, str2, str3, str4, 'bda', str5, str6, str7, str8, 'bcdef', 'aabcc', 'acbac', 'bdcaa', 'bbbbcc',
'babccc', 'abaccc'])
num2 = solution(['klmnowx', 'abcdefgiklmno', 'fgij', 'bcfghijklmno', 'fgjpqrst', 'uy', 'abceklmnouvw', 'pqrstuwy', 'fghijlno',
'mnouvwxy', 'klmnopqt', 'klmnopqrstuy', 'aeuvw', 'muvw', 'abcdeklmnow', 'fhijpqrst', 'mpqrst', 'klmnoprt',
'fghijklno', 'abcdelmo', 'klnuvwxy', 'klmnopst', 'abcdeklmnov', 'fghj', 'luvwxy', 'ghklmnopqrst', 'pqrstwx',
'abcdklmno', 'cdefghij', 'pqrs', 'efghijklmno', 'fghjklmno', 'adeklmno', 'rs', 'kuvwxy', 'ghij',
'befghijklmno', 'ln', 'hijklmnopqrst', 'ghpqrst', 'fgiklmnopqrst', 'pqrtuvwxy', 'pqrsty', 'jklmnopqrst',
'lnouvwxy', 'klmnoqsuvwxy', 'abcdeghklmno', 'fi', 'fghijlnpqrst', 'abdklmnouvw', 'uwx', 'abcdekln', 'klmno',
'abcdekn', 'abcdemuvw', 'pqs', 'fghijpqt', 'klmnopqrstuw', 'n', 'nopqrstuvwxy', 'abcdefghj', 'fghiklmnopqrst',
'klmnorst', 'abcdemnouvw', 'fgh', 'pqt', 'abfghij', 'o', 'nouvw', 'abcdklmnouvw', 'abeklmno', 'abcden',
'klmnopqrstwxy', 'q', 'fghijklmnoprt', 'klmnovx', 'abceuvw', 'klmnopsuvwxy', 'hj', 'abcdefgh', 'fhjklmno',
'klmnoquvwxy', 'wxy', 'klmnopqrstuvwy', 'kln', 'abcdegklmno', 'mno', 'gklmno', 'klnouvw', 'fghijklmnoqr',
'fghijpqrst', 'mnuvwxy', 'ghipqrst', 'klmnoqrtuvwxy', 'acdfghij', 'uwy', 'fghjklmnopqrst', 'mnpqrstuvwxy',
'abcdeknouvw', 'abcdefghijklmno', 'klmnorsuvwxy', 'abcdeh', 'klmnost', 'iklmnopqrst', 'abcdegijklmno',
'fghijklmopqrst', 'fghijklmnors', 'pqrstux', 'abcdefghijlm', 'abcdem', 'klmn', 'opqrst', 'ghjklmnopqrst',
'cdfghij', 'kluvwxy', 'ceklmno', 'abcdeghijklmno', 'lmo', 'bklmno', 'fghijs', 'cdeklmnouvw', 'abcdeknuvw',
'cdklmnouvw', 'abcdeklmnovw', 'klmnopr', 'fghijklmnopqrst', 'klmnopqtuvwxy', 'abcdefhijklmno', 'abcdeuv',
'abcdefhklmno', 'x', 'abcdeouvw', 'fjklmno', 'a', 'klmnopqrstuv', 'abdklmno', 'fghijlm', 'bcefghijklmno',
'quvwxy', 'fghi', 'klmnopqrstuwx', 'r', 'klmnuvw', 'kn', 'abcdeklmn', 'abcdeklmno', 'ps', 'klmnoqrt',
'pstuvwxy', 'klmnopqrsty', 'lmn', 'd', 'abcdefghijmo', 'fghijmnopqrst', 'ghiklmno', 'mouvwxy', 'abcdeghj',
'fghijklmnopr', 'kmnouvwxy', 'fghijklmnopqst', 'klmnox', 'nouvwxy', 'adefghijklmno', 'kmo', 'klmnovy',
'klmnopqrstuvwxy', 'cde', 'y', 'klmnouy', 'fgklmnopqrst', 'nuvwxy', 'kluvw', 'abcdefghijkno', 'abcdekl',
'fghijno', 'ceuvw', 'abcdelo', 'bcdklmno', 'gij', 'abcdeijklmno', 'klmnopqrt', 'abcdeklm', 'pqruvwxy',
'klnuvw', 'fijklmno', 'knpqrstuvwxy', 'fghijklmnor', 'ace', 'abcdekluvw', 'deklmnouvw', 'lpqrstuvwxy',
'abcdefhiklmno', 'fijpqrst', 'klmnopqrstvwy', 'mn', 'kmpqrst', 'ipqrst', 'fghijkmnpqrst', 'uvxy', 'bklmnouvw',
'fghijkmnopqrst', 'fghijklnopqrst', 'kopqrstuvwxy', 'pqrstuwxy', 'abdeuvw', 'acefghij', 'jklmno', 'k',
'fghijqs', 'abcdefghijno', 'fghijklmnort', 'adeuvw', 'vwx', 'gjklmno', 'hi', 'abcdefghijm', 'nuvw',
'fklmnopqrst', 'abcdehklmno', 'fghijklmnoqrt', 'klmnoruvwxy', 'abcdemnuvw', 'klmnovw', 'klmnopqrstvw',
'klmnoqtuvwxy', 'klmnoy', 'wx', 'ouvwxy', 'lmopqrst', 'fghjpqrst', 'lnuvwxy', 'vy', 'abdfghijklmno', 'kmnouvw',
'uvy', 'klmnoqst', 'klmnort', 'pqrstuxy', 'qs', 'lopqrstuvwxy', 'mnouvw', 'abdeklmno', 'abcdelnouvw',
'pruvwxy', 'qrsuvwxy', 'cklmno', 'bc', 'acdfghijklmno', 'j', 'fghijpqs', 'fghijknopqrst', 'fgijklmno',
'fghijnopqrst', 'mpqrstuvwxy', 'knopqrst', 'acdeuvw', 'lnouvw', 'fghijklmn', 'klmnouvxy', 'abcdefghiklmno',
'abcdefghij', 'hij', 'abcdekuvw', 'klmnopqs', 'aklmnouvw', 'acdefghijklmno', 'cfghij', 'fghijpqst',
'cfghijklmno', 'abcdefhi', 'kmouvwxy', 'pquvwxy', 'pqrstuy', 'pqrstuwx', 'ce', 'klmnopqrstv', 'deklmno',
'klmnouvw', 'abcdeno', 'fghijkmo', 'knouvwxy', 'fpqrst', 'hklmno', 'fghijkmopqrst', 'abcdefghjklmno',
'kmpqrstuvwxy', 'dklmnouvw', 'abcdefghijkmo', 'abcdel', 'giklmnopqrst', 'buvw', 'klmo', 'klmnoqrsuvwxy',
'uvwy', 'abcdeluvw', 'klmnostuvwxy', 'bceklmno', 'fghijm', 'defghijklmno', 'ijklmno', 'pqr', 'abcduvw',
'fghijklmnopqt', 'hijklmno', 'klmnoprsuvwxy', 'aeklmno', 'lo', 'klmnouxy', 'cdklmno', 'fghijpr', 'muvwxy',
'lmnouvwxy', 'abce', 'kmnopqrst', 'pt', 'klmnoptuvwxy', 'abde', 'abcdeghiklmno', 'klmnopqsuvwxy', 'klmnouvx',
'efghij', 'klmnouwy', 'bceklmnouvw', 'klmnuvwxy', 'ad', 'klmnoux', 'gjpqrst', 'abcdegij', 'fghijkpqrst',
'fghijlmnopqrst', 'abcdefj', 'fghijklmnops', 'fghijklmnoqs', 'ghi', 'fghijqst', 'abcdemo', 'abcdefghijkl',
'fghklmnopqrst', 'no', 'klmnopqrstuwxy', 'klmnopqrstvwx', 'abcdeklmnou', 'abdefghijklmno', 'klmnopqrstxy',
'acfghij', 'pqrstuvwy', 'kuvw', 'abcdehi', 'de', 'fghijpq', 'lmuvwxy', 'abcdelmouvw', 'abdfghij', 'knuvwxy',
'acde', 'cuvw', 'uw', 'kmopqrstuvwxy', 'abcfghij', 'fghij', 'abcdeklmo', 'abcdehij', 'abcdek',
'fghijklmnoqrst', 'pqrstvx', 'klmnopqrstvx', 'abc', 'klmnoqrstuvwxy', 'acklmnouvw', 'afghijklmno',
'abcdeklmnuvw', 'abcdei', 'fgiklmno', 'klmnopqrstuvw', 'abcklmnouvw', 'abcdelmnuvw', 'abcdehj', 'abcdefghijlo',
'fghpqrst', 'acfghijklmno', 'abcdeg', 'klpqrst', 'klmouvw', 'bdfghijklmno', 'aefghijklmno', 'fijklmnopqrst',
'fghijps', 'fghijklnpqrst', 'fghijklmnop', 'fklmno', 'klmnopqrstw', 'abcdfghijklmno', 'fj', 'lnopqrst',
'fghijkmpqrst', 'fghijlnopqrst', 'ux', 'fgjklmno', 'fghijklmnopqr', 'abcdeghjklmno', 'abcdefghijkmn',
'abcdegiklmno', 'abcdefiklmno', 'acdeklmno', 'klmnops', 'fghijklmnopqrt', 'fghijklmnoqt', 'abcdegj',
'acdklmno', 'abcdeghi', 'abcdelmuvw', 'abcdefg', 'fghijkl', 'gjklmnopqrst', 'hipqrst', 'klmnopqstuvwxy',
'lnuvw', 'ghijpqrst', 'pqrstuvwxy', 'klmnovwx', 'klmnoqstuvwxy', 'bcklmnouvw', 'abdeklmnouvw', 'fghijklmnopq',
'abcdefghijk', 'abcdefghijklno', 'fiklmnopqrst', 'klmnopq', 'npqrstuvwxy', 'klmnopqrstwx', 'abcdefi', 'lpqrst',
'ghijklmnopqrst', 'bd', 'bcuvw', 'hjklmnopqrst', 'adfghijklmno', 'klmnosuvwxy', 'louvwxy', 'bce', 'gpqrst',
'fghijklmnot', 'wy', 'pqrstvwxy', 'fghijkln', 'lmouvw', 'gi', 'fghijn', 'fhklmnopqrst', 'ghj', 'klpqrstuvwxy',
'abcdefgklmno', 'fghijlmo', 'fghijo', 'fhpqrst', 'klmnoprs', 'abcefghij', 'abcdeklno', 'abcdefghijlmno',
'kmnpqrst', 'fghijklmnoq', 'abcdefhij', 'fghijklmnopt', 'klmnopt', 'abcdefklmno', 'abcdelno', 'pqrstw',
'fghijlopqrst', 'bfghij', 'abuvw', 'abcdefghijln', 'ac', 'aefghij', 'prs', 'lmnopqrstuvwxy', 'abcdefghijn',
'klmnopqrstux', 'luvw', 'giklmno', 'kpqrst', 'jpqrst', 'fghijrt', 'fghijlo', 'abcdefij', 'fghijklmnorst',
'fghijqrst', 'tuvwxy', 'fghijlmopqrst', 'klmnouwxy', 'bdeuvw', 'fghijprt', 'klmnoprst', 'pqrstuvy',
'fghijpqrt', 'fgj', 'pqrstvxy', 'abdefghij', 'abcdegh', 'abefghij', 'lno', 'klmnopuvwxy', 'klmnouvwxy',
'fghijrst', 'cd', 'euvw', 'hijpqrst', 'pqrst', 'klopqrst', 'gijpqrst', 'klmnopqrs', 'fghijk', 'klopqrstuvwxy',
'rtuvwxy', 'klmnorstuvwxy', 'stuvwxy', 'abcdevw', 'cdefghijklmno', 'bdeklmno', 'pqstuvwxy', 'fghipqrst',
'fghijpst', 'kmn', 'mo', 'abcdeuw', 'qst', 'fghijklmnost', 'klnopqrst', 'abcdekm', 'abcdefgj', 'klmnopqrstuvy',
'kouvw', 'abcdelmnouvw', 'abefghijklmno', 'fgipqrst', 'klm', 'klmnopstuvwxy', 'abcdekmno', 'fghijmno',
'pqrstvw', 'kmouvw', 'cdeklmno', 'st', 'fij', 'fhiklmno', 'abcdefghklmno', 'lmnuvwxy', 'klmnovwy', 'klmnow',
'mnuvw', 'fghijklmnpqrst', 'klmnoxy', 'fghklmno', 'b', 'lopqrst', 'pqrstuvw', 'abcdekmouvw', 'abcdeklmnouw',
'acduvw', 'klmnoq', 'bde', 'pqrstxy', 'qrs', 'bcdeklmnouvw', 'abcdekmo', 'abcdefghijkn', 'kno',
'abcdefghijklm', 'abcdefgij', 'kmopqrst', 'kmnuvwxy', 'pqrstuvwx', 'fghijkmn', 'acdefghij', 'fghijmn', 'qr',
'l', 'kmnopqrstuvwxy', 'abcdefghijl', 'afghij', 'auvw', 'abcdew', 'klmnopqrstwy', 'adfghij', 'abcdeghij',
'lmopqrstuvwxy', 'abcdefghijklmn', 'uvx', 'km', 'abcdefijklmno', 'abcdeij', 'pq', 'lnpqrst', 'bdfghij',
'abcdefhj', 'mopqrstuvwxy', 'fghijklmnopqs', 'fghijqt', 'ade', 'abcdejklmno', 'fghijklmpqrst', 'pqrstuvxy',
'mouvw', 'mopqrst', 'lmnopqrst', 'abcdefhjklmno', 'acdklmnouvw', 'bcklmno', 'nopqrst', 'qrt', 'fghijlmnpqrst',
'pqrstuv', 'klmnos', 'pqrstwxy', 'fgjklmnopqrst', 'pqrstuw', 'klmnopqrstuvxy', 'fhijklmno', 'abcdekmnuvw',
'ghjklmno', 'klmnoprtuvwxy', 'abcdefghijlmn', 'klmouvwxy', 'abcdegjklmno', 'p', 'hiklmnopqrst', 'rstuvwxy',
'gh', 'cdfghijklmno', 'klmnou', 'iklmno', 'klmnopqrstvxy', 'lmpqrstuvwxy', 'prtuvwxy', 'klmnovwxy', 'pqst',
'klmnortuvwxy', 'lmnpqrstuvwxy', 'fghijmpqrst', 'ghiklmnopqrst', 'klmpqrst', 'klmnoprstuvwxy', 'ghklmno',
'fghijopqrst', 'klmnoqruvwxy', 'abcdeklmouvw', 'ae', 'abcfghijklmno', 'vw', 'fghijr', 'kmnpqrstuvwxy',
'fghijklpqrst', 'vwxy', 'uxy', 'cklmnouvw', 'abcdefghijkm', 'uvw', 'bcd', 'bcefghij', 'abcdeiklmno', 'klmnot',
'cduvw', 'fghijmo', 'eklmnouvw', 'klmnopqrstuwy', 'kmnuvw', 'lmouvwxy', 'abcdefghijlmo', 'cefghij', 'klmnoqs',
'klmnouwx', 'kmuvwxy', 'ceklmnouvw', 'fghijklmnoqrs', 'abduvw', 'abceklmno', 'ghijklmno', 'abcdefghijmn',
'bcdfghij', 'pqrstvwx', 'fghijlpqrst', 'gijklmnopqrst', 'abcdelnuvw', 'pqrstvwy', 'pr', 'fghijklmnos', 'c',
'fghijklmno', 'abcdefghijkmno', 'abcuvw', 'abcdev', 'abeuvw', 'pqrstuvx', 'klo', 'fghijln', 'klmnpqrstuvwxy',
'abcdefghijlno', 'fghijklmnopst', 'acd', 'gipqrst', 'w', 'abcdenuvw', 'deuvw', 'abcdeklmnouvw', 'fg', 'cdeuvw',
'lmnuvw', 'abcdenouvw', 'klmnoqt', 'hklmnopqrst', 'klmnouvwy', 'gijklmno', 'klmnopqrst', 'fghijmopqrst',
'kmno', 'f', 'uv', 'fhij', 'knuvw', 'klmnor', 'klnouvwxy', 'bcdeuvw', 'bdklmno', 'abklmnouvw', 'abcdehjklmno',
'bcde', 'fghijklmo', 'abcdefghijklmo', 'ko', 'abcdeklmuvw', 'bcdefghijklmno', 'beuvw', 'qstuvwxy',
'aeklmnouvw', 'h', 't', 'kmuvw', 'fhi', 'fjklmnopqrst', 'hiklmno', 'fhipqrst', 'qrtuvwxy', 'abcdeklnuvw',
'fghijqrt', 'pqrstx', 'bdefghijklmno', 'gj', 'abcdelmno', 'abcdefjklmno', 'fhjpqrst', 'klnpqrst',
'fgijklmnopqrst', 'abcdelm', 'fghijrs', 'klmnouw', 'fhklmno', 'abcdeln', 'fgijpqrst', 'fghijklmnoqst',
'abeklmnouvw', 'klmuvw', 'i', 'lmno', 'fghijklo', 'fghijkm', 'g', 'adklmnouvw', 'be', 'abcdefgjklmno', 'prst',
'puvwxy', 'qrstuvwxy', 'klmnov', 'klmnopqrstuvwx', 'acefghijklmno', 'fghijpqrs', 'fhj', 'abklmno', 'abcd',
'fiklmno', 'ijpqrst', 'fghijnpqrst', 'lmnouvw', 'suvwxy', 'knouvw', 'duvw', 'fghijkmno', 'bdefghij',
'aceklmno', 'fgklmno', 'fghijst', 'adefghij', 'fghijklmnopqrs', 'bcdefghij', 'abcdefghijko', 'klmnotuvwxy',
'klmnopruvwxy', 'klmnovxy', 'qtuvwxy', 'fhjklmnopqrst', 'klmnoqrst', 'prt', 'fghijt', 'uvwx', 'abcdekmnouvw',
'dfghij', 'abcdehiklmno', 'klmnopqrstu', 'adeklmnouvw', 'abcdefghijmno', 'klmnopquvwxy', 'abcdefghijkln',
'mnpqrst', 'fghijlmn', 'lnopqrstuvwxy', 'pqrt', 'fghijpt', 'abcde', 'ij', 'bcdklmnouvw', 'fghijkn', 'pst',
'bdklmnouvw', 'abcdeko', 'fh', 'fjpqrst', 'fghijqr', 'beklmno', 'fghijklopqrst', 'lmuvw', 'klouvw', 'fghijpqr',
'abcdegi', 'psuvwxy', 'klnopqrstuvwxy', 'abcdelmn', 'fhiklmnopqrst', 'fghijprst', 'lnpqrstuvwxy', 'qruvwxy',
'aduvw', 'abcdekmuvw', 'adklmno', 'abcdeu', 'cefghijklmno', 'lm', 'hjklmno', 'abcdefghijklo', 'klmnoqrs',
'fghijko', 'ouvw', 'pqrstu', 'mnopqrst', 'louvw', 'prsuvwxy', 'abcdekno', 'klmnopqruvwxy', 'kpqrstuvwxy',
'abcdefgijklmno', 'klmnors', 'abcdefghijo', 'npqrst', 'knopqrstuvwxy', 'vx', 'fghijqrs', 'klmnopqrstuxy', 'u',
'aceuvw', 'klmnopqrtuvwxy', 'uvwxy', 'fipqrst', 'klmnowxy', 'befghij', 'gklmnopqrst', 'abe', 'mnopqrstuvwxy',
'fghijklmnoprs', 'abcdeo', 'eklmno', 'fgi', 'fghijlmpqrst', 'qt', 'abcdefghi', 'bcduvw', 'bduvw', 'klouvwxy',
'kouvwxy', 'fghiklmno', 'abcdemno', 'pqsuvwxy', 'ab', 'klmnopqrstvwxy', 'pqrstv', 'abfghijklmno', 'beklmnouvw',
'fghijklm', 'pqrsuvwxy', 'acdeklmnouvw', 'vwy', 'ghjpqrst', 'fghijl', 'klmnopqrstvy', 'abcdelouvw',
'fhijklmnopqrst', 'klmpqrstuvwxy', 'abcdef', 'bcfghij', 'fghijkno', 'kopqrst', 'rsuvwxy', 'abcdekmn', 'aklmno',
'dfghijklmno', 'abcdeklouvw', 'klmnpqrst', 'abcdeklmnouv', 'knpqrst', 'aceklmnouvw', 'kl', 'fghijprs', 'rt',
'klmnopqrsuvwxy', 'bfghijklmno', 'klmnouv', 'abcdefh', 's', 'klmnouvwx', 'fghijp', 'uwxy', 'fghijq', 'klmnoqr',
'vxy', 'fgpqrst', 'fghijlmno', 'defghij', 'pqtuvwxy', 'dklmno', 'klno', 'klmnowy', 'abcdemn', 'abcdeklnouvw',
'ptuvwxy', 'abcdehijklmno', 'acuvw', 'bcdfghijklmno', 'abcdemouvw', 'abcdefgi', 'opqrstuvwxy', 'v', 'lmpqrst',
'abcdeuvw', 'abcdekouvw', 'qrst', 'klmopqrstuvwxy', 'prstuvwxy', 'lmnpqrst', 'pqrstvy', 'abcdfghij', 'klmnop',
'ijklmnopqrst', 'klnpqrstuvwxy', 'klmnopqr', 'xy', 'abcdeklo', 'abd', 'klmnouvy', 'klmuvwxy', 'abcefghijklmno',
'fghijkopqrst', 'fghijklmnoprst', 'ruvwxy', 'm', 'e', 'abcdej', 'hpqrst', 'bceuvw', 'fghijmnpqrst', 'pqrstwy',
'klmnopqrstx', 'qsuvwxy', 'fghijknpqrst', 'bcdeklmno', 'klmopqrst', 'bdeklmnouvw', 'klmnopqst',
'klmnopqrstuvx', 'acklmno', 'hjpqrst', 'abcklmno', 'rst'])
num3 = solution(['ysvydhncudvxqgub', 'jxomzgqmpccovmyy', 'hxiwwqdowwbdzrql', 'zqfykhyqgxpuedhx', 'vhszanyizlocrcta',
'dthywqimclejyrxf', 'pxvnsacefcaeqwpn', 'eibroystpzgkhwkt', 'efioczniyhzlkgxx', 'jbafyifjrdsevjlt',
'noggsbrxuzxxxpnv', 'usxugdobkxyvebgp', 'omppygjbdzvfncoh', 'lszhxcyfyhbezqpl', 'sywbjmfmigsrdhbe',
'kmitesfpzturedvn', 'fhccayoplynamcmf', 'xwkxxvmngwdkktcq', 'bkdetlrdtrvxtwnm', 'otbqjkibazuiuzjc',
'bvdlpsuozpxykhso', 'sfkdemywenvutigi', 'zlsgexavkjlbniyz', 'omvmljrelegkrnly', 'ncfqxwbgspmmxequ',
'nsnusovrqfyjqcmi', 'xmfltlmbucykoygu', 'znevkwdmcjkxazvx', 'qmmlumphgweyuqll', 'vvwllhnjjilkkfbr',
'tfczebbrmcwkijpy', 'dyqudxtooxmzaivg', 'qabmbvkkacpipzwv', 'ousivmwzqkzowbsf', 'wiajbnzcyczvdkme',
'jtvkqglawuiitvne', 'hynkguvzlahiaweu', 'dcdhzutcxsrwhtiu', 'sjkbkfbzcltyhkzc', 'vmtoulenvyzgmzph',
'hhpjlqospgyrpjnr', 'trxsiqvzjdsumnbx', 'ifmzrmfjlfbxrspp', 'zuybbnxweoodzrcp', 'dqselcmauqpdbvji',
'ucdmjxlnodsqbtpf', 'yxqxoqyqsuxbvvwh', 'jifmvnffunc', 'jlgdux', 'fttypgxftlzhrjhu',
'rzmkqtaejgzrwvht', 'fylzmnvoslrjeuhu', 'xxhmsywcfchxybtz', 'nivviopjjkilmfnt', 'vlvtonhigprfttuk',
'cwgnurrfabcfotdmj', 'erjxfseyzaygaujp', 'nrcqdwczglmcvinq', 'dqbyglmywihtexid',
'vqggccuiimjqqpuz', 'wbvvklwhouxxcbzg', 'jxstdmcbouqvysje', 'envdnanmuewgheqr', 'oxjeneckyoxdypwq',
'ityoxogkfmlasgfq', 'tgpkcweywtqopjnc', 'hepoijpjgvckkqzc', 'ubppuzmagmjgmjnf', 'snvaiqinphtkbxtc',
'wvdwymqejrygisbn', 'kmbwjynfbwyablvs', 'rsscpinfcegvnulj', 'oplzudhvjaumtavx', 'oionhndcrjvfexir',
'cxxlrudrixtmjsgw', 'sfngfbrksewwbwuo', 'wngezcjkxlftmure', 'xgkmmsvjjvtlwyko', 'dfaihamfjrwobkai',
'ybzlbmtejcbhkbqn', 'yvgttkpmodjrdjaj', 'wsfkdifjxsisyazp', 'btdahuinzvvmyuti', 'sppdjjphoadtnxqz',
'idikaxmkupaaeyvd', 'bxmusrwhsuglelsa', 'wllftkyuyjwumzfz', 'lsrfakcruqfghhqr', 'oitbsfztaayzgttw',
'qvdaclqbkxzxtvji', 'hqtnylqopcuyitvv', 'dovrsivynjuycgob', 'zbeexmgffbvgyukt', 'jnyrkwuketocbnlp',
'kesivzsfimkupknz', 'fvctuhkhcsxgpnlc', 'geyiflxobsqqgysp', 'vdhnckkljiwiylkc', 'jxixmpjvkuisogjx',
'ggmgthlqqfjzvsiv', 'nkdbbqswrytidodb', 'cvnxasfxcyyprwky', 'msptawajcgigotxx', 'lggqfreicrrzgqug',
'pywexuvmpapzhhmk', 'yjfzlaazckdxqhpk', 'gxopiqnejwahizvy', 'rwptjuqhjshtosim', 'zhszbxltmwjfbcnn',
'hznbmqrhucjlhtev', 'repwvulbjzulzqlm', 'juemhyiaujdhjwda', 'iphegtklhgyiabcof',
'tpqxoalgjntzhxph', 'ahnrxtoyzqrqrxce', 'ljsunmfpleczezfi', 'flqbbwjpvmpiagkm', 'enxrdnasgsrczncm',
'setirvmdopdbgqqi', 'uuyoeqtcgvygmlbd', 'gznmxhdzpgclmmce', 'wrqmvtilsmjrfruj', 'nzbqahmftsbygrje',
'nodxqfwosevxikai', 'ynzmckxtfampkdcb', 'ishsysxcjavxukfq', 'mbwcnmktksqoptdx', 'ybpgwitxuarhyuud',
'odkhmislpnpjltvc', 'imlknoihasmgbjle', 'autoweexfbmsnamc', 'pzddxvvmnmujzovy', 'zbklmwsqltyiqjaq',
'wsfezmwlwnovzfnq', 'ipvtflaxlabczbjwg', 'xmeypiupgboeikma', 'qmhxpnusoafktsrp',
'akbzwaoevusmqhjy', 'ptnrluxfiaoedirs', 'fkkujjetvujaffev', 'iqlaebkqlabcuugvd',
'tvfazupnodyxyegj', 'cxxbmckkoocwwmkv', 'eiinwggrnufbuefm', 'jbajzgyvabcjrpirb',
'anotitqeflusqkmx', 'kkyyjfyqfwuyphvs', 'mkxxxgmewnnfmtgw', 'rfzfkowvhlbuptnn', 'yihacnrktjrrbupi',
'ljbfbmrxivbqhvgn', 'kelkifhcummieqec', 'qwglfqmlgtufeggt', 'ztdsjupiobdswepc', 'nxxrjnqebfrtztab',
'zwuijitgzkamuohu', 'skctyqbrtdlybrad', 'ftvbzzqisluhwvoj', 'tkyzlbdwikxwxtfm', 'yqzbwtibgyhezefc',
'ugmtditxujqhzdjk', 'pzqfxlcsbyiayoqn', 'mvuvmubzxoapqlwq', 'wxydvrxojyifgild', 'gaubuvvoncoahhqs',
'arrqgidasqpyozqo', 'hlktmcpfqmqunsiw', 'hpshspcjtkvjtyfc', 'xwdjpdyqbgkvbbto', 'dnipqamvliabetfk',
'zrptncovohuprjfj', 'zykerhdnpwqnklnp', 'wehvwpjsjmlhbxme', 'qhabvcixedhtacnm', 'nzbonhjtiragsjxu',
'piktfsxlejzjpmxa', 'kpgluxplomivhups', 'utbqkkbmdakmajvb', 'pbosjdvammowabof', 'hwwpavjyghyogxiz',
'qixjbuehpllqwbir', 'watokwdhqrlthmyt', 'fiuvnmucwsfhvirt', 'efjbktqktzylkzym', 'eyagoufvrlrbukvi',
'dbebcdxywrceoioj', 'dmejkiuqtpzkvtil', 'irxxxrbxjvvisefx', 'ezacasyffovrewri', 'zfoernjrzvxkzqjn',
'krrmkfftxdxqxrjf', 'xexiopshwbkipjdw', 'cnuiizhcocljycvu', 'idsxihqjacgtwiuu', 'nwjjtbiketrqdvxb',
'avmxhxabcxhflzcbs', 'uqxjgosfyjcbxshz', 'gwybdcsgvjjacjoq', 'zokabcujdqyhfvvve',
'dudqkxdyvnmzxbal', 'duurelhvlvlwtisc', 'vvduznkfxsydjjsu', 'jvohyxbezkxdybjk', 'tecmjpqvbqdfgbch',
'wmiwtqmxlipobteb', 'bzhfoutsommbeahv', 'pzxilyvfyokfmsmr', 'fvptnoujoahvjljv', 'nntjwlzvtlwjijtq',
'iiahigptxppvjwwh', 'fiwxrfkvznhngctp', 'hljuecxsqwhfhooj', 'kpgylifngxbybkwm', 'ckxgbjjygzkystat',
'anxjpmmadenhxunx', 'kztzbysfhebhkxhw', 'qeywqntlveiebhos', 'jlbvhtvumiyxwqlo', 'ubsttmdcjigfizes',
'tifeodqhusljfhxl', 'xhtrvehthwvsxkmj', 'slytykltdhwruorn', 'ettsedvbbxttpkwg', 'znlstbcrbxxyauvt',
'zvxkminzbadeyxpn', 'vkeqpqwrdrzvrdkg', 'lmgvnrmbwermpsxx', 'wpcihvumyumoljws', 'sqqleapevuisjovs',
'xrtefpneewlrlvwd', 'mmbabccilwfyvvjak', 'mqebclxzlkierkjf', 'cuytrwygyntgajgm',
'fhodjnmtmzrqzszj', 'kmgwmlnfykcuvqnl', 'aopjewaqievtqdct', 'tjouxksorchkworv',
'ncirabcozpldzewjz', 'sucivpgmovkfqxpn', 'akhusibommljkvfb', 'cdxrtkejlxftegjn',
'pcykwqocqfjcpygs', 'ddgipyltjxtthplq', 'uqtqauyppkzzztxr', 'byziilqifrkefnmx', 'pihmqvosbrmfwvgj',
'zcrokjgwuujlsqzk', 'midiigvhwxuuxdoj', 'quzizelifvrqgiqy', 'qoizxtjfeiykktbh', 'kopvmoiueozhbxfe',
'rabczignulcwpsobz', 'esmkumjwclulmmlg', 'cwknucjbjropshgm', 'xrkvscqbnuofxbbd',
'lfhexistfbnypjxb', 'qtvceoxufqerkgcd', 'nvqnrbzmizbmenoj', 'vaxeseydjahzmeqv', 'kkhvyzvdlupbekot',
'ghkdrqrrufndvlab', 'puuorkmgkyjrrfzm', 'qdojlkfsajazdbtr', 'trunvamzxxtruqqk', 'wyfqiycmuaxnwdmj',
'tehftxcnimfcgulv', 'xideohbursltsyaw', 'zukuxtscehugrlwz', 'tqyowyifdxmlekmi', 'gktvxxotbobtzjhz',
'sbrdswxuitwshrql', 'vjxkqyvipqlevbhk', 'xupvseicxsjlvprl', 'zzvgmaspjzobbbai', 'umqxughwbhxrbgnv',
'necgnedkdtsxllws', 'kfzhgtbffdkcmemk', 'jygmwohqgxytdabcc', 'xubntcuzhakycmhb',
'nykkvobihcvcbsom', 'jmpfjbgethlvegac', 'rcrkrqlqszizkuwn', 'mkvtjvezpqntwsor', 'vavxnwabzsvbxrta',
'wxjtawscbrqldboj', 'ukqyxnzmmregydtj', 'bzdoqdhyfxjhrtca', 'zwwifjejxilnlncq', 'zbhinfwhbsewmmnj',
'wpatetlrcetrwygn', 'qijjqtjtkjldjzpv', 'wizlmxgtbqokdive', 'gjowgwgtfyoyvakj', 'dutziyzhjwwdwbmh',
'hhxlvaslalqnjfez', 'nftbzbqrrdhpbvel', 'rawgbwriyffuvwea', 'qelvbxvcmyipiyux', 'gpvbmgzpjpvmfjou',
'edysbthmpzewjmhq', 'gimdgabewrjfmouq', 'kabamudmytcvskgz', 'jnbqnbtzepeettut', 'ubycgxbczobyuvty',
'ncqlwqzzlurrfurm', 'mqdliidaptajnque', 'aqkislhbhutlmskx', 'kqgowgleasjmgjro', 'anzasevxbinscrwy',
'mligzlmekbqjtlkz', 'acjwzeaariolohth', 'lewbaeswgtsegzgf', 'bkaleiidkzgtyukg', 'griqeggfgygajdxr',
'tiqtuoakcxhsppug', 'djwebkqgutgcqjkq', 'mtdquygxxpcnmxvg', 'lzbitojuuxxhrcms', 'wkqdzfkdeoxlrrrv',
'qdkvpynqxmqizxfh', 'rsypvochupieijuw', 'zhjqkrovsdewbwrg', 'cojrovhotitqglxf', 'vupizqllrxepdyej',
'rrcescgfpodyqgqj', 'enyhpwibqizxzxlf', 'ysgpfnkxewxpunmc', 'qqayjdiwesfhjqdj', 'vvxsqmsxkwlowkaz',
'vhbgvteemnjcjzjn', 'pjvysfsrgpzeefgi', 'hjpqwdkuxpvojlrb', 'qdviqqkpfpmusqku', 'zekclapatdchkkuu',
'ushhsykosapkwfvn', 'qlwhigtykfafzwkf', 'ueeemzyxxionuzvh', 'uxidcslniryrlkfr', 'wjrqpxvnjwnzvhaw',
'sfufkmlseobjehmb', 'viqcfxqgzfgjlwyn', 'vfffdaynlllgflud', 'xgbzqwuziammugee', 'juwviucofrqykbph',
'nfhofnyrvpgnrncr', 'xwnrmtztbduhaxzm', 'qwjuwencytcviddt', 'zgtzokhuophlklax', 'yhhhyqbivjulhxzz',
'qjlrmtnkpezzxbip', 'csjtxagscqzcyxgw', 'gibiwnkxfwmdypdb', 'zwuqefypxjswiqnr', 'rvwoomgislxnjiku',
'avtzjpgdqkrswwil', 'tybnjxlyeppveuln', 'hvjlkwgdbzjuthio', 'uwmvnynpvcrtjaoi', 'tazibajxbbektuny',
'eydtgcsqrjeudusa', 'cjvzwcgypecfudux', 'oovnezznsbbuzage', 'jjeciyognokzoavb', 'ewwzxbjfxgyrwdnz',
'mqtotsnaejvwsfxv', 'hewhemklxufjlxds', 'qfgrjckxuvxppffa', 'xrkanxmmdhjnrpms', 'ugszqiazpribuhin',
'hhtlbstnuebaovan', 'wmerwupitfwffwjq', 'cfhlftbplljrdnmt', 'iwgvszqjzoutyofq', 'rfddyjwanuajwfms',
'glcpwdgghxjjlbhl', 'opyabchjxtqeaqluw', 'zqrzsgsurxcablbp', 'tlzsuhpazrgyftra',
'hfbywjxrjvfyfjor', 'xfuisoaqkhitaneo', 'jbmpkilwrfevuabc', 'riftearjllxbsrpg', 'visatalbyphvpcqn',
'tezwyeuynxiqceny', 'gmllnngsknyuqfyg', 'jcptptnztjtczgin', 'sfslwzsttdrouqmi', 'oprcoelsndlnehzv',
'cfmhxjwgozohudcf', 'mhxzekxwbbccbumx', 'qeqyvhpujfgrmiop', 'gtqtcpovarcorjrf', 'aloszdzbbywgchfd',
'dknbhpmmjnuehczn', 'ebkeuntykvvfywib', 'nlgiglojmpbxhafl', 'uswobtqjlbukbjdo', 'deinrxindafjewms',
'bgkkntzoayoycmii', 'ibgusyotlezfhixr', 'jhduofjmetuvulfv', 'ncomoknshtsctgif', 'oeqgwqzgiuxzwnbo',
'kfqhheuvmfwtbokw', 'iqsoqygphhfktibu', 'bobacxbmnfzanumt', 'knnwtzpjwzujuuxw', 'vfnlobdgwymhcgun',
'gsvqncqugmzlvkcc', 'fqnfjzhlmmsjzvxx', 'isynioqvlkzdhldw', 'ysyenabcioynjgrzo',
'mgarisubmmtmxaqu', 'tlkplxdwjvivozqu', 'uumvkpkfqckauzpy', 'jqzzndmsdwuznmii', 'cqqaephdukcklkkh',
'arqsbqajtlzbxspv', 'fpwnogjkszhusmqn', 'arkauhwcnzyhgzgp', 'mmlbhlqmmpxdsjpr', 'hxsyiwgylwvfxvqf',
'fmgsmcxhczkblvrr', 'jfsbaiqqmrcqziyh', 'yonriirnykgcqqoa', 'loqnbxhvnqhefnzc', 'vnrwfrtawnjzmzpr',
'nwvmixbdevbawgcb', 'ssoscjougdkdgwzy', 'tdotnfxymskkechy', 'gdqyqjahcohateim', 'nmpingpzculglnzq',
'oshxfncaghkzfflo', 'brqucwymtbtbpkmg', 'dlbolallmawftyne', 'zaygaqdomkdndypz', 'frynwfgjeyczjiyj',
'fkrmnqytsxookgtf', 'ztsuspdffprgefji', 'urmvtcqxbzqlfenp', 'jtqnervrgeqgltma', 'mxazffkgorgqvasd',
'ohxmmsvrbcbakvtz', 'gvgbadnzvabrkajj', 'ytxszlngumxdrxgs', 'uyrufyweypbkrbcg', 'ylelxbcmvwdqlsst',
'fnqgyqxovwwitolz', 'nmrqcgovdmaregoh', 'jabcyxscsxpdwhduv', 'agyjbfjdrxsdxcbz',
'rsxthmvbbfsbapza', 'bnulsywwhvtckkmm', 'oetgshifgdhknjen', 'fdacdxgrjnfqhbgl', 'ltrpuqvqvaaijmix',
'aalhlxvddlhxsyev', 'qubggjexevkjzapf', 'qffkqkgvbxyrncum', 'ouebeyqrrbwluaiu', 'bsmvockhhfxdvwnn',
'wzyrusboriskzetg', 'qtkohvlnoxldzkhe', 'sknqielwtnmdozdk', 'hueabhcqpsziqofs', 'qvdcptldvpyzwbwt',
'gmcsgkgfgdzvdywo', 'whcybgsdsunkkpqd', 'zouenychsloywadi', 'ofnixothejurjqwx', 'baurihhbpsuzaxdz',
'odnxgsawwegaqqsk', 'avnvjxfrofflpnfl', 'fpeejbcasyuuirri', 'lnqcckixeovoabad', 'ogzfwbnpmoqzdxqb',
'lsfpkmktczfkgase', 'ckfkwbmenshnuzrk', 'puuxkxfbbtdttkec', 'oxplgbgxocgwayuc', 'tgxfplgbhcjubdtg',
'cpcwhsckcdfhbwmp', 'huaukdwwqenjsnbr', 'hvofxghsjlfhswhp', 'vnwbsvtnpfpwatiw', 'mcbkpsbgywhqxsix',
'zksceqawvnemisil', 'ojpmvjelrldcqflk', 'ppfxcvjrjywbkaci', 'vkkkabrzumejtwdr', 'jzzvegddqgtogyel',
'fvwxxwbukfrbazxg', 'rpvgsjrcsunopqja', 'ngjxvxsqxcboieeo', 'xgrdakguxugvngjr', 'zlixckrlsfjnvwiw',
'kqqahdzvaovwrarw', 'zeqmlrqvcymohkfc', 'fkdmammoniaqeaei', 'ktrvrgxstgvttftq', 'skujpfmasgqboljm',
'ydenwjcdlcdtodqp', 'hgsuqywmnwmyfotr', 'waufauuijgxaqceu', 'gbudfydfhbvoamth', 'afskwqlszmvafeqm',
'nbsjuuyfqbhqajok', 'iiawyxcdikosbwsx', 'kgqvvxhnmswfngde', 'icqcdxpedlxpvgms', 'wpxzbdlhhvarycks',
'wkwdjgkzzrmuhuol', 'swsgbdcrbhqhfcci', 'kgmkgeiryynvhwah', 'cmpvksdyjvmbdfhj', 'uglxrzjgijfcvhbx',
'bgevfvpmocxgausz', 'uqojyggipoyuwkby', 'avlnovzpuzubuuss', 'eyghurrorndubcsm', 'zdnntbwcugnykdti',
'lchrlndexvovoznd', 'cpnizzfmpzinymlk', 'hskvkurwexwqasxt', 'xprysdqnfmvifwjy', 'ngzdbejzpatoixnp',
'zxomsbqlfuhemazl', 'iqvuegauwclhvqma', 'tzdgvyptuayjvktt', 'zvhbvljserqbcbir', 'mukwzypdxlegwipe',
'uslhhogibvwqzhyz', 'rylrlapnfsdogovl', 'impmhoqumkogchoq', 'zarlqxhzfwhqjsms', 'ymxpexvboiwzkomy',
'nhgexfzvunjnosgb', 'wslojqmvusvumclp', 'uufkkyrchehmokjr', 'uadbebqfwaewmzdk', 'wwzazyhamqhdwjzc',
'yrwrqxhvmzfeiqpa', 'gycblakmiqqoioke', 'gpyfmbzhhhtuysyf', 'agtyhlalmwzmpnes', 'jhbfquwnkzzmmrqg',
'xahekbixkfaidgkb', 'njiajqrymsbxsfyj', 'xrhkzoerfwjjjvyv', 'mojaewgjwmmxmmcj', 'mcimexhcqqptnotx',
'lshefqasobmbuxdd', 'srgglcluxgheudmy', 'cgxocmkqzjagwgmm', 'iyreabcwxbnkpsjoa',
'zaljaqjvfvvqdays', 'gskeygtjgbijvkjn', 'smpslnyxjvbhjyvh', 'raeaxhedueaayvlp', 'vbzqcqhzdaptsdts',
'enurfjqxyapakpyu', 'xesnqtvzlkjudkgx', 'kjwfyrasqtafiyri', 'bsbavcxzjuaksbld', 'hstmbonbgsleppae',
'exyhezlohmqkhxlr', 'rqmhckbvtfyqwsxh', 'wfnvwsffbdliqsll', 'eaqnrvadjaojgfsm', 'rhocxroqdqrervjn',
'mzdczcvbrhjwcdve', 'yxlrftymqxqtbvso', 'baunrbrfzrapqzit', 'oipmrdynelruxvry', 'khppolojdkojxwqv',
'umwgrzharatzdqjb', 'jbabfxajhdducgsw', 'ohtxxfqthypvhbca', 'knwjiwadhywkwlsz', 'qteikhwuuasdyvpn',
'ytdeibtvnlysssfj', 'bdcflvlghfonjfik', 'eactaiaqtgrhwkbn', 'evfodntmumnmpltz', 'zklhlzjiueabafnz',
'zrsbbgkjcseqeang', 'cbvthkbgywxvjkhh', 'gykehthvmdzklzmm', 'bhrydwsdwtqaxyhu',
'abchczaihcevacgzx', 'yonhiezjoqwosrwx', 'lpwsvvjbtimkqkaz', 'tibcufriphwxwzhj',
'kqxnnvmxdyubsyma', 'jdjdalrfdvtzjzzf', 'qzijzvthlydyayby', 'xsmhbxalbihmkgmr', 'ickheeqdhkhfvagy',
'zgancfyzdspdikye', 'rglysjgxdhtlirpe', 'xwmvbwnbknuynzms', 'rtggytyubuthyvdu', 'hjfqzmmiqdopyduc',
'yyeixxunfkstmdly', 'stccdhodaeauqskv', 'bsemgaskpcgvmcgd', 'todqxrxzpksoowqy', 'wqpfgvkppuehavdx',
'oecawvidnbencfzv', 'ocpbksbgdutggshn', 'hvfvfvhuwftqdtys', 'raqymywkbzpjsomo', 'mnsgyltrdguifeom',
'zrtwkfvmrxgmebpc', 'esnlddvhmlycfnzm', 'ujmrrippyxxaitjd', 'cjqopvqjmwdwrhtc', 'axterdjcgvvkvjmt',
'wsfjhyhiwcskrnzl', 'excxprrgtvsdstkq', 'bqpvnpcbqbjeorfs', 'zgrbyxqcahdirxzz', 'ibruhcuhiwpsndjo',
'dmningijzetvgssq', 'vsbnskosiigyjwhd', 'gvbexrsmzefdfjra', 'rnjdwommvluzgmiw', 'qfnpnioafynmfnch',
'iutdykdyrnjbijim', 'yybpzynyyvqsibqw', 'ukcumxubdajklbow', 'qpfhjabesozcqxnt', 'ogpjowmcxjvltaei',
'nmmgxxpblhyvjcza', 'rsdicjpuitrhjhoo', 'rougghrsdcuhaxkb', 'ccoubobkldovhdha', 'heeysansiaiqecsy',
'txyzgixqzbqoyddo', 'zgonqkaonzusldmu', 'ksvocdxauzvzaqej', 'tthfhimluvparxna', 'jrfaqfteargbowaq',
'vwgdxfzukfkbwmoi', 'kxaxverroublhnkg', 'hxcyocruwhxerkwv', 'waaywxwtrwpnwcxe', 'kbrwbedcrxacnfzn',
'heqhjudnrfmpgffr', 'zoninmtmgfzwfivy', 'nhdjsbedakglczfb', 'eyklkfsriufgdeta', 'cdtcihvzlfrxcqkk',
'nszlmuisqibdhuij', 'frfwwwunnpwouryl', 'bahmwsfifpehpvlm', 'xinovuwjryvjderk', 'stdxirugdjwsxdrf',
'ukzsodimorlbassb', 'dcqdmnpirlwetexz', 'lnkkravbrdzuaixf', 'iqhikikqgoabcupoz',
'tqqnskydlxxyeloy', 'hoqhujloveotexob', 'tafrmbzoiiyxkrpv', 'gedftcwddbvqbcbp', 'tmlvgfxezfqhqlro',
'omkqddentowyusgs', 'uvmoywmfgcxprcob', 'wxaexnkxfscqpbvn', 'arouwkkwzmpxcraq', 'oshuiowfgoxvscum',
'wlcbjlvtpwbizxkk', 'pqdqfcardhablnlm', 'hncftotfykwkmcwc', 'ilbkfisyjvqmmjox', 'mjziuevwvgazkmrr',
'qxftpuleqzgeoxkn', 'qwfbcoulervauwzy', 'hzzahmyatnakmfkm', 'atlkeburbqttzgdv', 'chctjbylvaqivhnu',
'kljxzdlufmjsakrn', 'ldqznwrdmigxmplj', 'jnzsugujwghliiyj', 'davvfzptwjezrtut', 'ayvxlihyfxjghbnj',
'damnybtgbouyhgvm', 'xycclwykeleqgqbz', 'xcexkuimhauveeep', 'alawhglfqmrpujdu', 'ucqkzhnxzfmhrscm',
'giqfhrubpvulkbcz', 'ibjyvrczdfvorhxe', 'qbwwxgvtphqitwrc', 'nznctodxeivfdauc', 'gcelouuuaxwxmvsw',
'rqelrfgexnkdnazl', 'fbepvxtrhujvrdfc', 'iczbfakdstudncnv', 'qwyjcjokwchroxbr', 'ycjrzaetiivrrdkc',
'hjaflkntduxbssgu', 'rwfrleciyxwvxygj', 'pfkodbjvlrgvryzh', 'fyvawqjluonvjjxc', 'nzkedkvundnsfmnm',
'zkvlbpsldcyafkpj', 'hrnjhejkhdkcmnmh', 'sydwdkxfjjkvvbfk', 'ydznqbenlyrstgmu', 'katzotudzcpwwvkb',
'xucadxwemqvixtva', 'nnbzlmlmesntwwhh', 'sidmvrqryepebkda', 'zqlfnaleybermqpx', 'kduaxanohkcebsaj',
'jajuaudbrkkcnyyq', 'rhtefiqjirzhpjwt', 'tgbyhnyxxivxpebp', 'oqqwgmpqimqnjrxz', 'tptopmpejaaaxokz',
'rglhbkxoupbeqxhn', 'diannxikfirreuin', 'ilkjfpwdabcorejuk', 'tzygwhlicpqhsxsm',
'ednqyfigrhjjsixi', 'ichtvcqqxhzvwyrk', 'ckyoxfbufktqznpj', 'xoskspafepfgeeit', 'jcbtyhklimaasdfu',
'cfkabckzjghzapvxx', 'owdyarpowhkunwhy', 'etnyrgssgohswpva', 'ccdzytrxkxrfobiv',
'vxmwodlmkjmnanqf', 'lfoyuzoffzuzknom', 'avpouwwwczpcsixm', 'befuilgwreabcsjqn',
'wwlkjupnpinaskti', 'wuaufrnozwrcwrux', 'ddmlqscfylvvlqet', 'ngtehvarjqltinad', 'hxilufvmpbmybqse',
'sxckpnkpctadurmj', 'tkauepahazlgunce', 'wdnczbubbvaeugur', 'blbtvambkabhgfmt', 'hscywaqlqpzmajlw',
'kqbcyrflffoyrrde', 'swatgwoezppbhzrz', 'wncpezwknhwlkyfa', 'fxoalqugauheullc', 'yfejaqfwodcbvjxo',
'srdidycbfudekvry', 'wbmqrnpsbwvajyst', 'eojhwvsjkhruoihy', 'lebgsqpfytyfljzy', 'nlfrksicpahzoyzs',
'vwfuihhrcdfzahuq', 'zxossokxsiilrhwn', 'nnogzvnyavbajgxg', 'xudcsovkwdigfykp', 'oxnernpkebnwtzgk',
'lpkluymjfczcabbg', 'xwmoythsnnalagrd', 'bwxqduzhwponwuxh', 'tvqujorvigsrzqra', 'ruhirwfwnudvhndi',
'yigakwntqrddbxel', 'doyelkmwfiqrcvwf', 'nqepgxvwmpczbqmp', 'euwsrbwhhaosbuxv', 'qybvertwzftjmsbo',
'ovrxezhfnplztkrf', 'zhsklztsgdxqqlos', 'hjkalxuedegqevxf', 'acqcmxxnvxiyiarj', 'irfjxvnxvcwfggyf',
'ivjlvhotuhyjrbqi', 'ybowwazfbqnlxhix', 'rwldwkwiuokthyvd', 'emeoryhhzmchkcaf', 'wkjtfktltlxrpodu',
'zozxqufosbvhvzmk', 'kejjywawtflpnzxq', 'tgjqeqqyflstgyfn', 'edodalhdkbpbvbbi', 'svvbrdqtivcocuok',
'jqycfyojmcojaike', 'uysmgvolzqhvrjcg', 'jepqutdjnzdxpuis', 'htypdjotmvugsqrn', 'ruanlnsslyvcmloa',
'rmguapshfylrqcyw', 'idmrozfesprjyydi', 'igiijxxuaewkngez', 'mmfbpbxhjbbtaktl', 'wbryhbistnsnxcre',
'eyypsgultocxkddt', 'hmgsapmnlbhkldjy', 'srdiuczmorzzmqmx', 'jydlzvjtvssbiriv', 'xyxlubdngtpamnie',
'hzxhqmvdfeelavey', 'dnmkfxoqikbpnncm', 'uvykqjhcbjrkhwws', 'hcouhxnefskqtsmj', 'tlzdfixqvzmpnxey',
'bqthxadcjbuoihjb', 'amqcryxqrquugjds', 'kazopbofkzigbrjf', 'yoazjvgcjnuynogm', 'cekiuyvsxvnhllot',
'skaakenhygficler', 'vyyblxbztgjdxemi', 'cwijfnzpasohsysb', 'vxshtpkflepkegsv', 'dqlajjejvwkljffm',
'pdrurythrunegiyt', 'wyniiprlwdxayecx', 'onzimmmmwsczxrud', 'wahjycyykcusbzkh', 'pmxfomqplrchaeji',
'cuiofjxjmfwmwjpo', 'mqeyxhbjjhtyiqax', 'vxjtwryiiaiqmgxc', 'rpxhygecrrxsorep', 'pdhcrtkvutpxkjqk',
'xghqzhfjrcskksay', 'llatzvkvpehtkmlp', 'evcdafiqhelayolh', 'wnpjllgpnngclefg', 'cplkciggvoivrdrk',
'rwzojlohceoksqei', 'ibblbsqbtieahuip', 'rxymbuhpxlybbpwj', 'oufytsooclpjthdt', 'ladsdwyczkhlprsk',
'lqglakcncwvhbmdq', 'pvffqrafetpcnonv', 'ltxqocyoaqwqlclh', 'ujleyjgijrzxpohv', 'hdliszkijxjfdhuz',
'uerwlwcboltvibyv', 'frnvgotjrsmsvdrv', 'kprkmutaqpumileg', 'dyfntcyriixrbzpu', 'pljixloqwehtiyju',
'guvbkiuixwtllbyh', 'aywoiniduriovexc', 'xkhsubtnkyitnjuu', 'orgjwbnwirxnlvkv', 'tbnfpmbwrdvlcids',
'ljptwryckhaervnt', 'piklsbpqrpcwtkax', 'btjqiwzsjhtyrabp', 'xaqhoeyrofnixysd', 'ildloryxoleksykm',
'tpkrvszvlfvhpgua', 'uomslwptxjarrgtp', 'qfawaceubqhtfqia', 'xvsatjnexaphrcsq', 'chlowdcammoiqswp',
'vryqjuplbwlaomsw', 'zkndhkyqnmooseqy', 'oehmlodyfkbgwggc', 'ygicydiozmvrkjov', 'vffghaadldklcvpa',
'dudkmcpnwktzabcyc', 'cgpwhbxlqbydfial', 'xkeqyrbppiqzzdtc', 'aywomxmmicyapqry',
'qxrfswxmtgqwiaiu', 'ogesstqnbrqzcike', 'quvgbtgtjtgxrqez', 'ilrohxbbjzdyifwb', 'mwbgfsetpneteejs',
'awvqavqersnsgvym', 'lslutwvxqsgrasxf', 'hujsniqoktvleeph', 'tbibnfjtibcusfqc', 'jkeeyrhwuudkrzmx',
'rckpwpavcgvgmbqn', 'drzbjsuvjgfxgpzx', 'kmdsvposrrdokxzu', 'lapmakjdxbobqslx', 'awqhcznyrcbreinx',
'sgtrrbfxpgcdmlfi', 'hjvvuazaydvuqzfl', 'ukvueksttoovtqnx', 'fjcjtxrbzsrxelui', 'ynxnlswchgyljfah',
'ueznbslrhcswvlvg', 'ixvfnmhdbnowsido', 'tnvrbemiduyabcpgf', 'xicjxbvnripjquxk',
'pnguepiandvkkjgm', 'fmjuyijqtflklzrz', 'wowbwesqdjgbnfza', 'bzhqulhhfrmvlikt', 'xwwbxkpqwzuvbfcc',
'tzfeejglmxpjfiob', 'ttvlzzgyydwznuuj', 'zsaqdcbxiivqeibj', 'jqhivhimzrbhfjye', 'woxtmnynlehbynso',
'tweacunvvzvxvkhe', 'wvjiwrdllmbrzyzh', 'kpawpohuffukizip', 'culggzusblbzrbvp', 'rfiaujemuathqnrg',
'txcebmnimvozhnbq', 'lbpnqjkgkmqepuca', 'rqfueobyxicwpkao', 'rggegjcjqzhrkjqn', 'xbxlktpwwsergaut',
'lhowgnysedqhcquk', 'oqldregahyfprwsi', 'dizcwcthvgopgnwx', 'bzpodvsqzlmeakvy', 'vclpieckqkxhblhl',
'lnvngowxjpgdkwfv', 'yvkdxviywwowawba', 'zxymzgtfqsshclgz', 'boqkrbmnsxvbiema', 'hoeexawhwjrohbxe',
'luocnssrsnrlbmyi', 'tduuyggdvgbfgmhw', 'frvhgulszabsrunb', 'vcsontpzpacsgobo', 'kaiqymcnijuixgvp',
'vgfugfulxkppkurw', 'foudqjgejntrwhke', 'abldoxtbpltfnsni', 'kqxvgbgkkoakfeaj', 'rdkjzlwcpygzkshq',
'qfjxzlkyrpmuvlrf', 'depydkicbtuwrbuf', 'vmpfhqfgcyreyqdl', 'oneokdfkplafayzn', 'fjcerifwgajithlr',
'gtlxawvwmlmqsuuu', 'wgfxdchxqlzdxcpr', 'ajdrspwucswacivi', 'wjzhtgddolhaahmo', 'hbyrafvgohzefptw',
'roxblqysntdnkfqx', 'rmvrjdkeppblcmvy', 'xzgbkvnyxljluccp', 'dvvwfjxmydfdzqyt', 'kxxjltlgbaiguihx',
'rahukefeaibeekpq', 'spsdfgpofpoanurm', 'pjmewktbcytjsvrs', 'nhtbcrwqzoxbhkyi', 'eanjdepcqzqdeoea',
'ujhvaizclocaksng', 'tkucqzszyktwvyjq', 'dnummodkocgrdhbx', 'bzvvgfxvgzqjshji', 'ddctbuygjncstchf',
'mrpciqjmowzdjvsm', 'qhdgxhopljagfbfi', 'ksnimciprjexohfu', 'sdfgsfcwgaknzrqt', 'keiywmjuavometzf',
'pxdzshicopwmofxl', 'xdwlukdaxhwjojeq', 'krnlgjtxhnuntwsa', 'bpnrhdwfkagaubka', 'beoyleogpryyjcmv',
'rrhlmtgpyfszchsi', 'ozdknlljectjisdg', 'wdobdazbwjecqcep', 'jfxjpbzonkvxltib', 'fwcffctkbvpkgexm',
'gornbkdvwuqirrlk', 'yyiqngwrxevbwchf', 'ggyqhxvbjwyzuxwf', 'ixhwkhgotdmkamtj', 'dbqqdygrhtysgxgw',
'mzwmkjfknwfhulgv', 'xtngfkkjuaonbemi', 'vghhkblxwbijsqwi', 'fkfulljgmpkmvxwn', 'kqdckewxfcwyjkuo',
'msaxmgcjerovxgqo', 'bswhhcxiljhjeivr', 'lwllrzomgnjzjqxh', 'gugxbiwfpjbtscyw', 'mmqsxwrnsiprrmyv',
'pdjccwbewqxbhgzn', 'mshemwgzytwmqljx', 'moezekitiafkvsqr', 'edthrvvafeypjypw', 'qspowcqalsukqhhy',
'wasrmlhgjgalcbrb', 'dglyfamnfpqkmteh', 'xgpvsclrqskbjnao', 'iawgyqoqnmxmwtrk'])
flag = calc([num1, num2, num3])
print("最终生成的 flag:", flag)
|