TPCTF2025 re wp
TPCTF 2025 wp[复现]
没打,只是复现一下逆向
chase
.nes 文件是 NES(Nintendo Entertainment System)游戏ROM 文件,是一种经典的游戏格式,在CTF中偶尔用于考察你对模拟器、ROM格式、6502汇编指令集等的理解。逆向 .nes 文件的过程和普通程序逆向不完全一样,但也有方法可循。
FCEUX:强大的 NES 模拟器,内置调试器(断点、内存查看器、trace log)。
Mesen:现代 NES 模拟器,图形界面友好,支持调试。
IDAPython + 6502 插件 或 Ghidra + 6502 支持插件:静态分析。
直接打不开,出现 Truncated input file 通常说明 IDA 解析 .nes 文件时 没有正确加载 PRG ROM 段,这是因为 .nes 文件包含一个 16 字节的 iNES 头,而 IDA 不是专门为 NES ROM 设计的,它会把整个 .nes 当作纯裸机器码处理,导致分析失败。
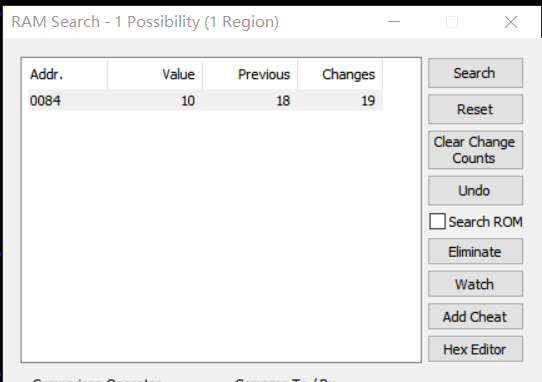
打开了还是看不了,算了,玩了下是个闯关游戏,既然不能IDA直接逆向分析,那么可以试试CE去开挂看看
不知道为啥CE搜不到,只能用FECXU自带的
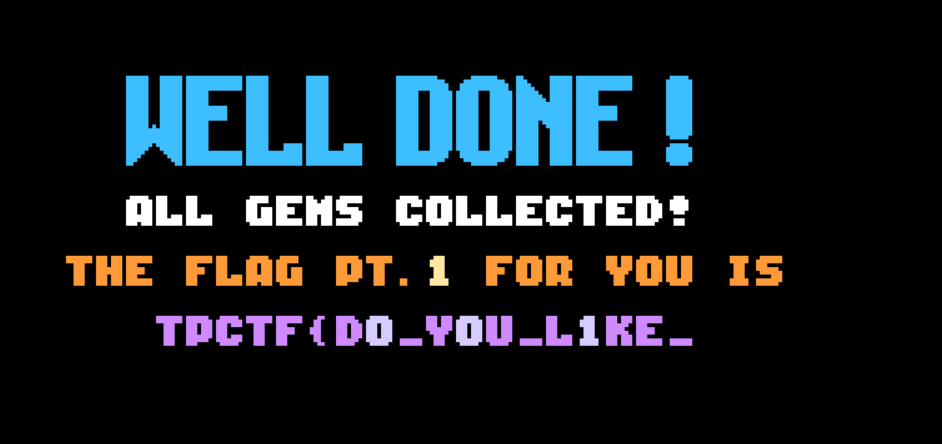
然后看了下0x83是要吃的数量,用cheat改成0x1就能通关了
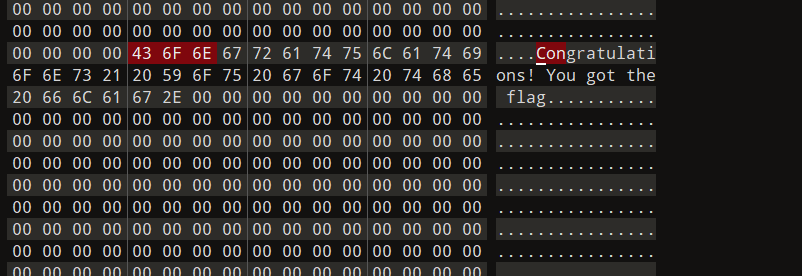
只拿到了第一部分的flag
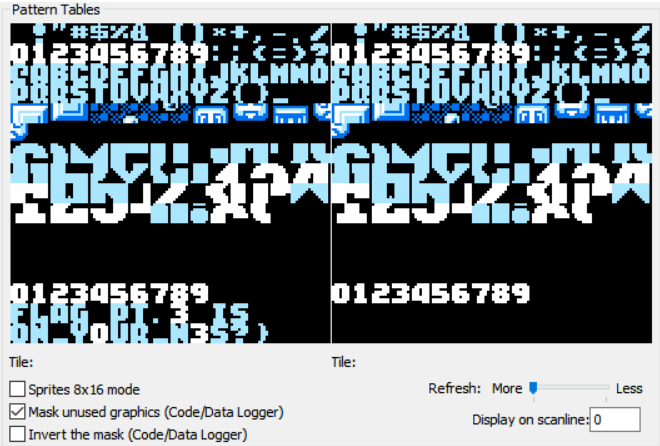
第三部分,点击PPU viewer即可
这里的右边是符号表,在 NES 中,屏幕显示的文字和图形并不是 ASCII 字符,而是 图块(Tile)编号。
- 图块编号是一个 字节(0x00~0xFF)
- 每个编号对应 CHR ROM 中的某个 8x8 图像
- 游戏用 Tile 编号 + 属性表 组合成一个完整的背景/界面
我们可以通过PPU Viewer查看
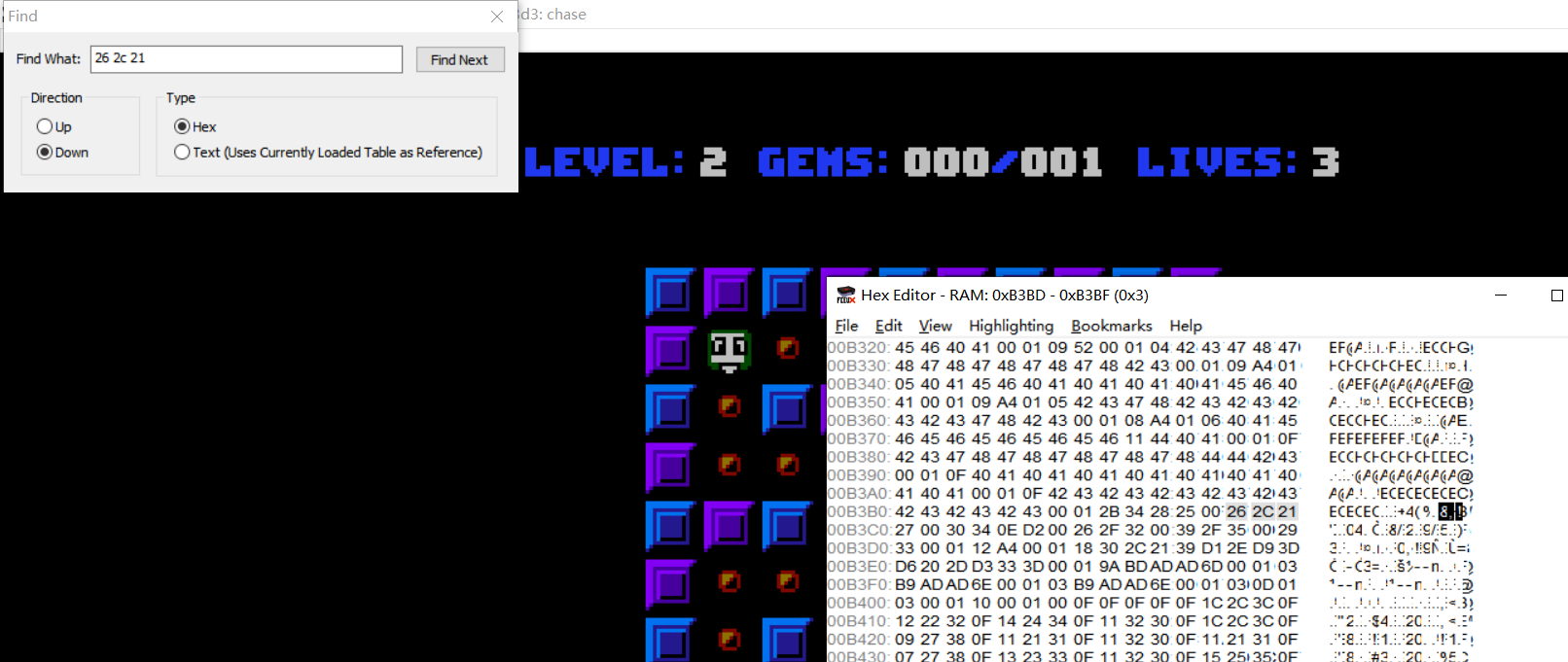
搜索到了第二部分:
1 | def parse_tile_string(hex_string): |
三部分都有了
linuxpdf
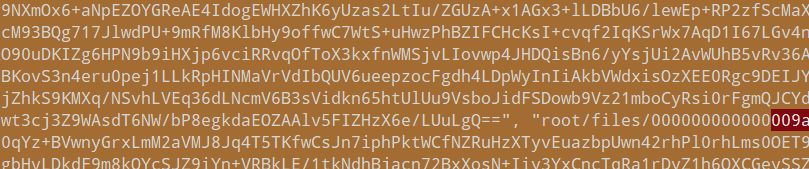
其实运行后我们发现,Flag字样出来时是与root/files/0a9这个文件同步的,猜测可能相关
下面标了源码,跟进看看
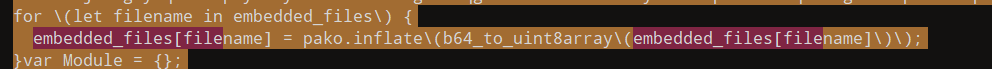
先base64解码再解压
直接对这部分解压也行,或者直接写个批量脚本
1 | import json |
直接ida打开(8.3好像不能F5,用9.0)
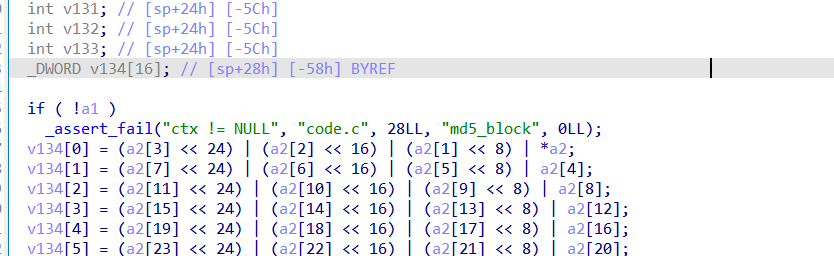
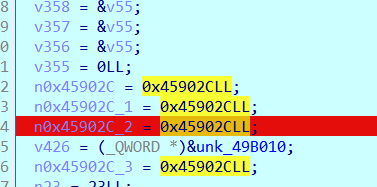
字符串里看到有MD5,跟踪下
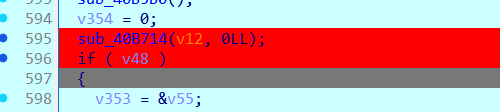
主函数读取29个字符的输入,调用sub_2948函数。sub_2948函数处理当前字符串的MD5哈希,并与预存哈希比较。unk_4008 是预存的一批哈希值。
这里只有28个md5,由于每个都是单字母的,因此爆破很容易
突然找到了
可以发现规律了
1 | from hashlib import md5 |
TPCTF{mag1c_RISC-V_linux-PDF}
stone-game
玩不了了..
题目还是挺简单的,简单来说就是给了七个部分,每个部分都有1-100个石头,每次可以取每个部分的若干个石头,看最后谁取到最后一个石头谁就获胜,总共100轮,赢了90轮+就可以获得flag。
1 |
|
TPCTF{M0nt3_C4rl0_S34rch_1s_4w3s0m3_f0r_g4m3s}
portable
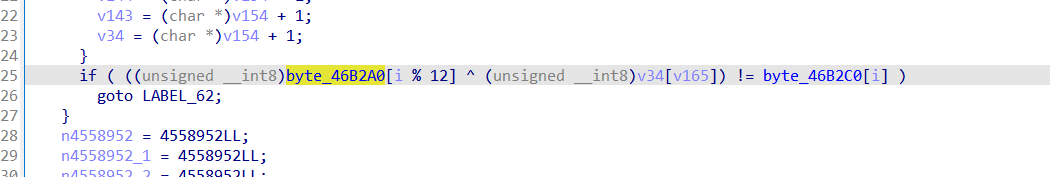
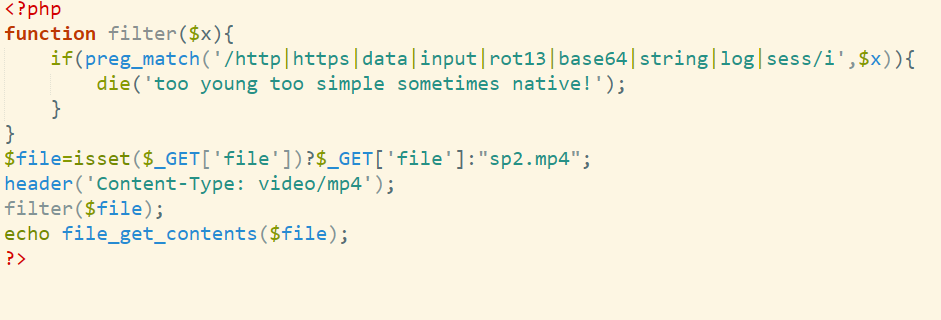
无法交叉引用就直接找立即数
输入函数:
后面调了半天,估计还有长度的判断在下面
往下翻发现几个可疑的byte
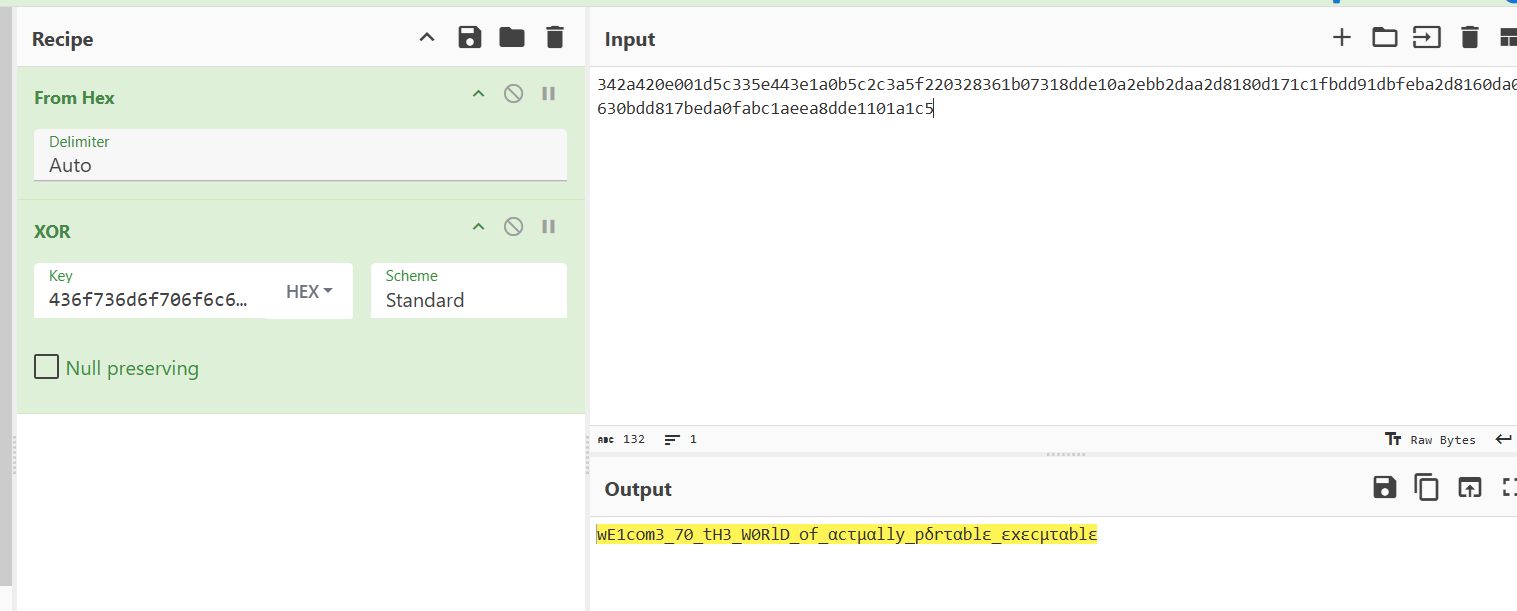
试了下直接出了
记得用github的厨子,不然显示不出来
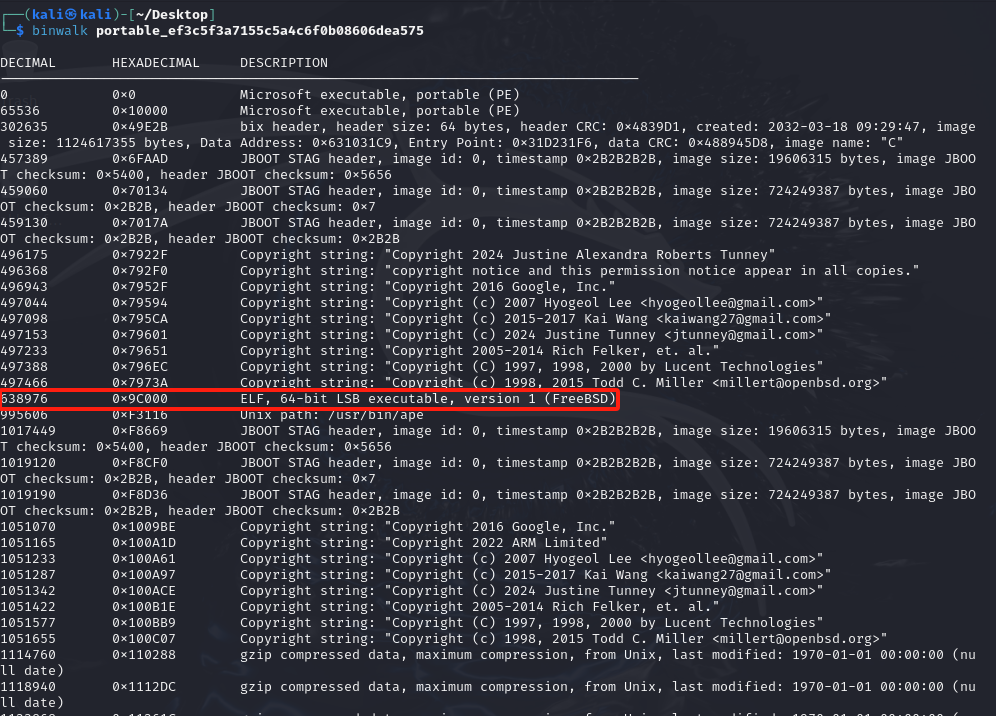
该题使用的不是传统的 libc 而是静态链接的 cosmopolitan libc
而我们手上没有它的符号信息,所以库函数是几乎没法分析的
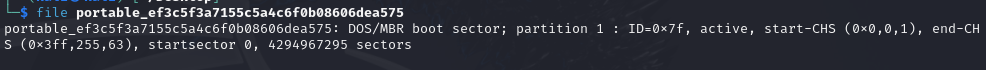
这个 file 命令的输出表明你分析的文件是一个MBR(主引导记录)引导扇区格式的镜像文件
该文件:
- 是一个以 MBR 格式构造的镜像;
- 指定了一个从第 0 扇区开始、大小为
0xFFFFFFFF的分区; - 分区类型
0x7f是不常见的值; - 极可能用于某种反取证、混淆、CTF题目或者特殊系统用途(比如隐藏或加密文件系统
0x9C000 ELF 64-bit LSB executable (FreeBSD)
1 | f = open("portable_ef3c5f3a7155c5a4c6f0b08606dea575","rb").read() |
再导出的dump文件就能交叉引用了
magicfile
又不能交叉引用
1 | __int64 __fastcall main(int a1, char **a2, char **a3) |
1 | sub_58E0(ptr, &off_119B018, &off_119B010, 1LL); |
从程序提取出mgc文件 第二个参数是地址 第三个参数是size
不如直接010打开
TPCTF{YoU_AR3_SO_5m@R7_TO_cRACk_Th1$_m@9iC_f1le}
往上找规律