TSCTF 2022 wp
TSCTF 2022 wp
baby_xor
1 | enc = [18, 20, 7, 17, 4, 110, 10, 58, 25, 124, 32, 14, 122, 6, 123, 22, 100, 8, 6, 48, 4, 22, 34, 117, 27, 0, 36, 18, 40, 4, 105, 42, 57, 67, 43, 85, 13, 60, 5, 83, 19] |
baby_upx
1 | # 给定的 dword_140004480 数组 |
1 | T |
多试几次:TSCTF-J{$uch_4_BABy_UPx_pr08L3m}
或者记录官解方法dfs提交,还是手动比较快
1 | import subprocess |
byte_code
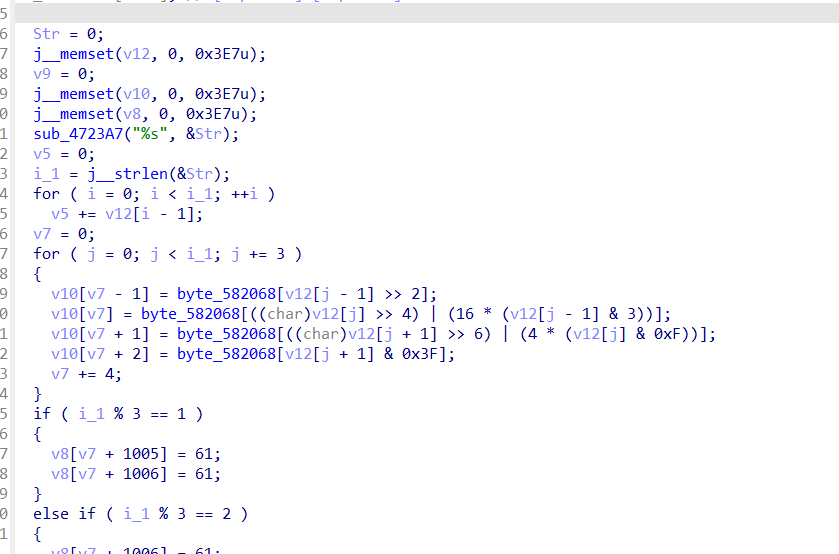
挺简单的,ai直接缩了bytecode里面的逻辑也挺清晰的
1 | 12 326 LOAD_NAME 0 (a) |
比如这段,就是a[i]=(a[i]+d[i]) ^ pos[i],STORE_SUBSCR就是给容器对象(list / dict / bytearray 等)里某个下标(key/index)存值。
1 | def main(): |
TSCTF-J{bY7ecoDe_I$_nOT_so_HArd}
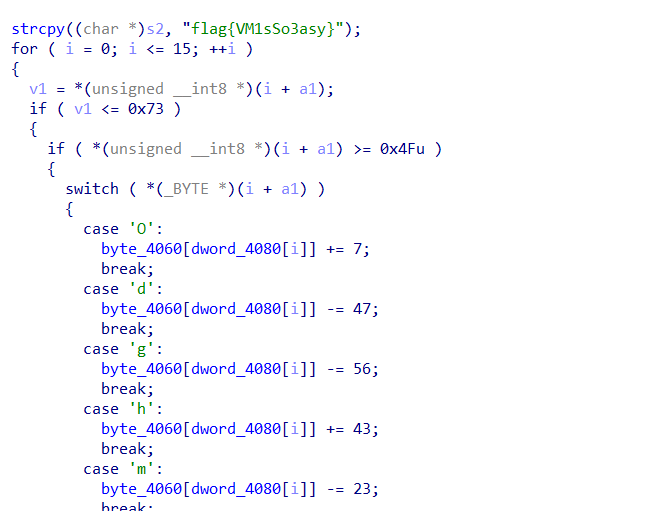
baby_key
先输入密码,有个类似虚拟机的
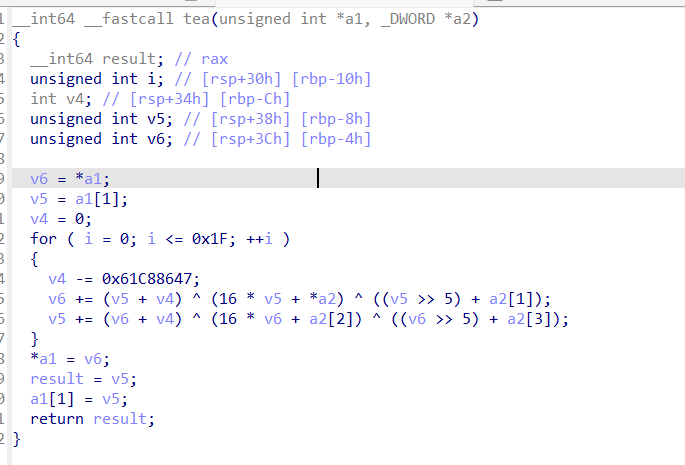
tea然后端绪转化
一开始的密码就是key要满足相应要求
1 | key = 'flag{VM1sSo3asy}' |
1 | 102,108,97,103,123,86,77,49,115,83,111,51,97,115,121,125, |
好在不多自己稍微看看就知道了
比如102-79=23那么要输入s才能这样便
可得
1 | sO*h4hdsOm3!!sg! |
1 |
|
加密出来是乱码,发现,init做了xor
TSCTF-J{T1ny_eNcryPtIoN_4LgOrIthm_Is_so_FUn}
Link_Game
19260817分才能拿到flag,用CE没找到…
只能逆向发现是个C#程序
看了下动调改分数也不太行,看来只能手动分析算法了
1 | enc = [53, 71, 22, 108, 73, 97, 59, 107, 63, 126, |
TSCTF-J{Y0u_@r3_1inKgAm3_M@2}
ez_maze
这个迷宫不是+1-1要结合地图来猜
关键在于:current_position 指向的是「走廊里的空间字符」,而不是墙、也不是格点。这个 ASCII 迷宫是用典型的 +–+ / | | 结构画出来的,每个逻辑格子的左右两边都有竖墙(|),中间是一整条空格。结果就是「可走的位置」在同一行里呈现出这样的周期:
|···|···|···|
^ ^ ^
(· 表示空格)。可以看到,相邻两个可走中心之间隔了 3 个字符:从左侧中心到右侧中心,要跨过两个空格和一列墙(这一列墙在 ASCII 图里是 |,但一旦没有墙,那里就会是空格)。如果这里有墙,那么 < 对应的字符会是 ‘|’,于是程序就会直接报 “Wrong Path”。因为 ASCII 图里竖墙就是占据那一列。
所以虽然表面看是 “减 3” 有点怪,但结合地图的具体排版就很自然了:我们其实是在 3 列宽的格子之间跳跃,pos-1 / pos+2 只是用来扫描两格之间的那条「通道」,确认有没有墙挡住。
bfs
1 | import hashlib |
DSDWDDSDWDDDSASSSSDDSSDSSDWDWAWWWWASAAWDWDWDDSDSDDWWDDSASSSDDDWAWWWDWDDSSDSSDSDSDSSAAAAAWWASASASDSDWDDSDDDWDDSASDSSDWDWWDSSSSSSSAWAAWAAAAASAAASASDDDDWDWDSSSDDWWDSSSDSASSAAWAWWAASSDSDSSDSDDSDDSASDD
Flag: TSCTF-J{1C34207F7C0B2F2C79A28A13B16907C6}
本题用angr可以去混淆,记录下,下次学一下
官解的dfs版本:
1 |
|
记录下:
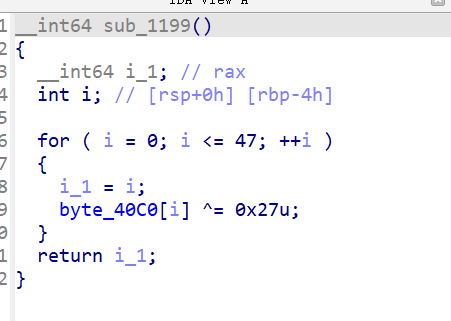
这里给出混淆脚本(-199):
可以考虑用 angr 去混淆,建议的参考学习链接:https://bbs.pediy.com/thread-266005.htm
Thunder_air
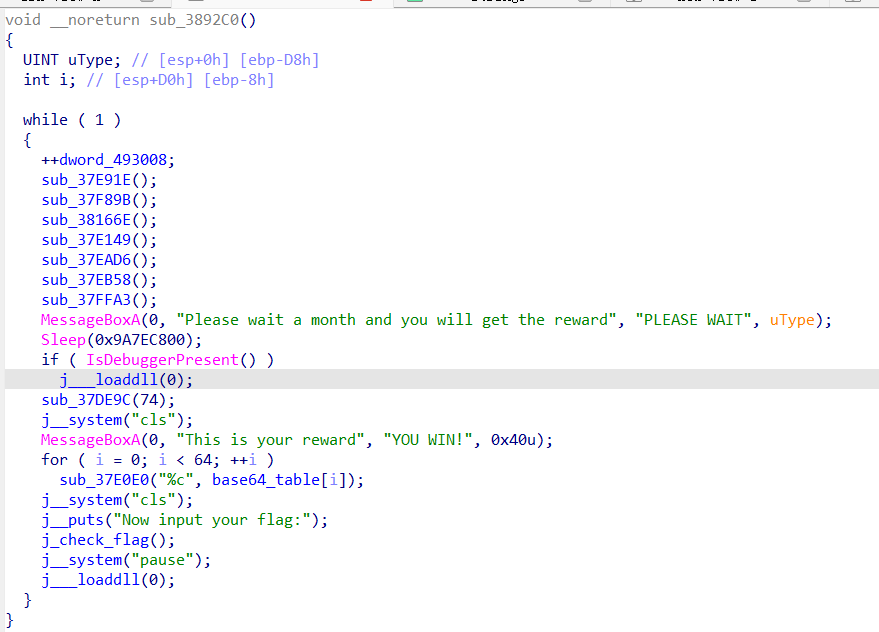
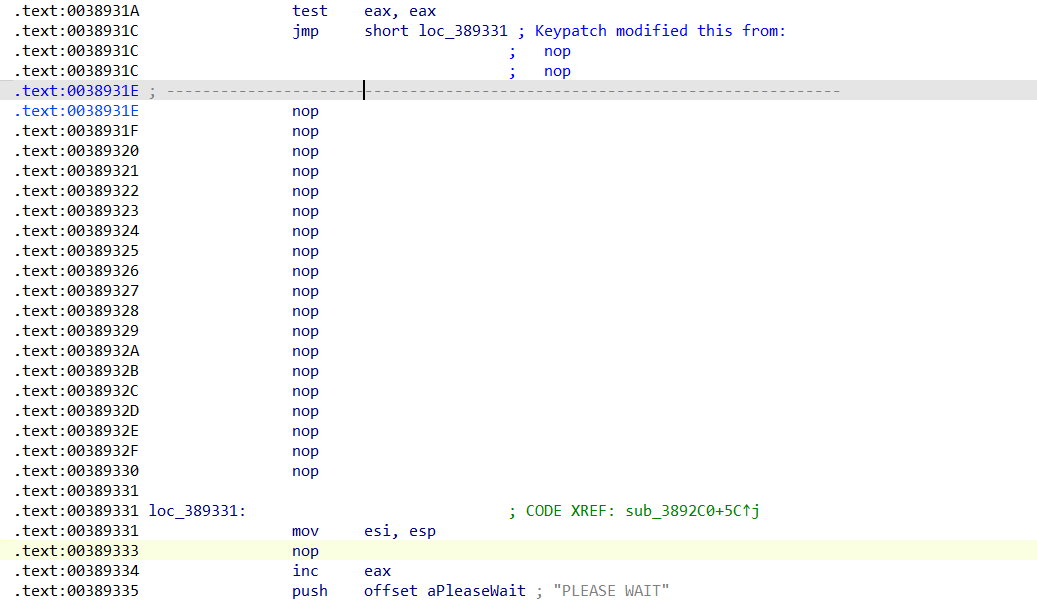
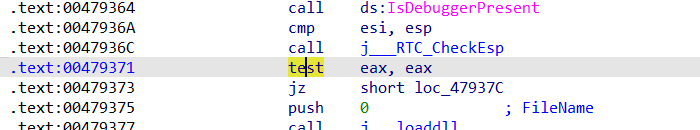
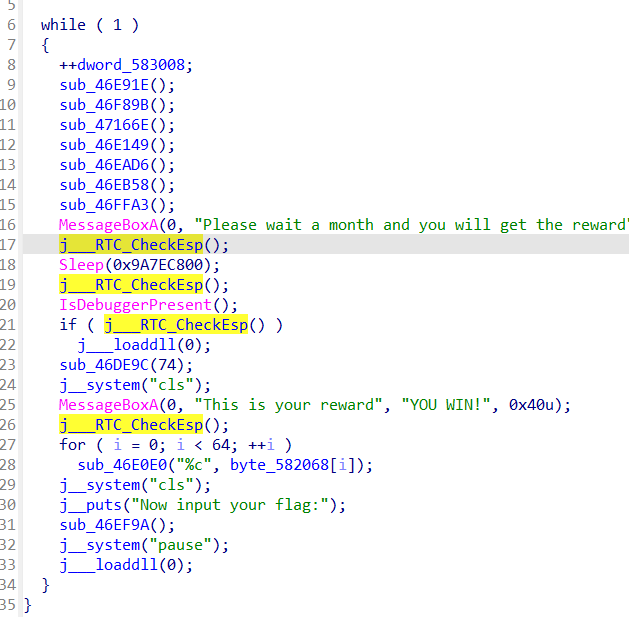
中间的调用非常深怀疑是不是混淆,还加了很多反调试,好像还有花指令
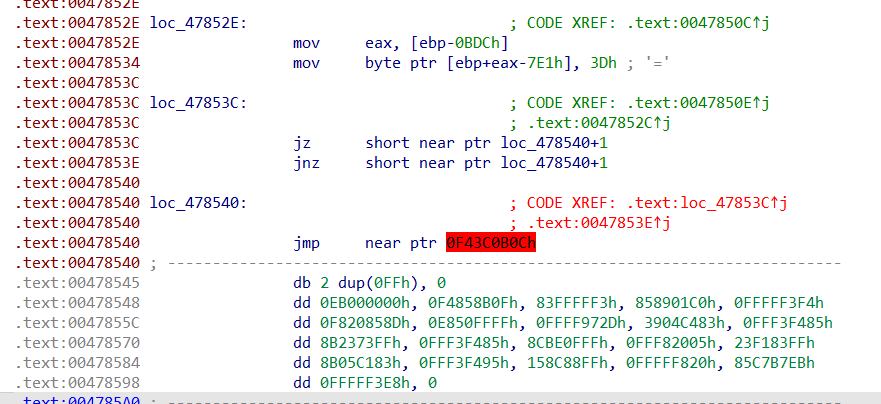
先对0EB…这一段u c可以看到生成了一段代码
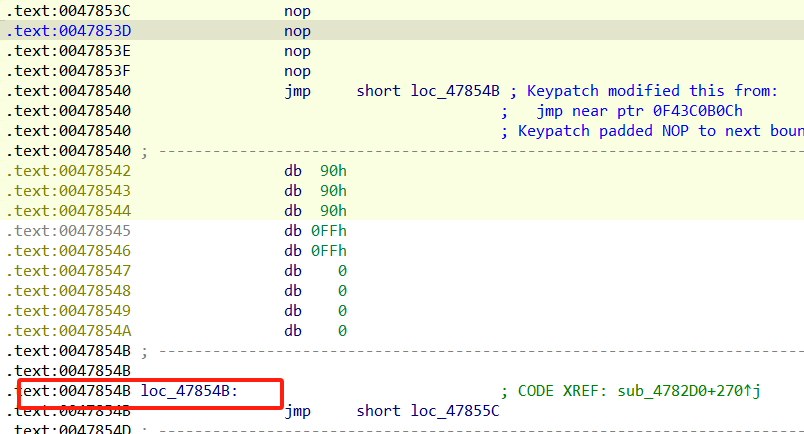
再把jmp near ptr 0Fxx改成
再把上面的jz两句nop掉
对方法ucp即可F5
前面还有个花指令
这么改,把sleep那两句汇编nop掉,下面的test改成xor
就是把这几个checkesp和sleep和isdebugggerpresen,nop掉
提出来就行,我这里没记录了
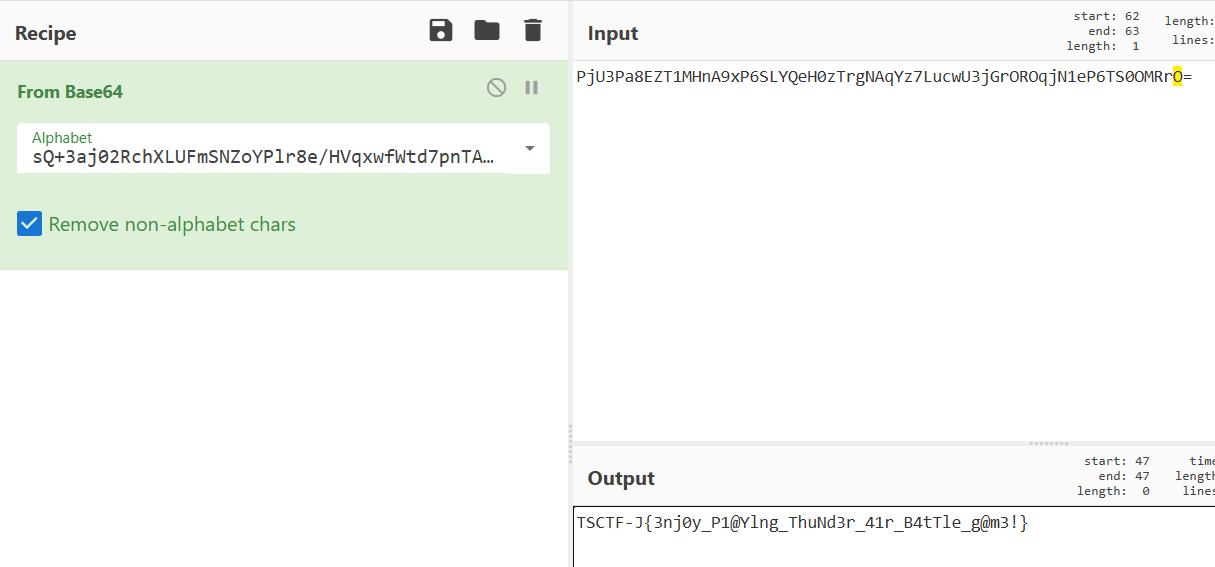
TSCTF-J{3nj0y_P1@Ylng_ThuNd3r_41r_B4tTle_g@m3!}
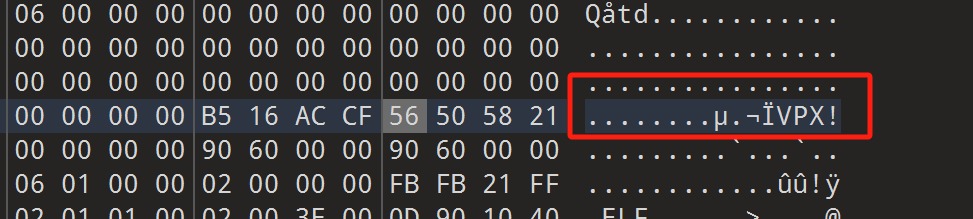
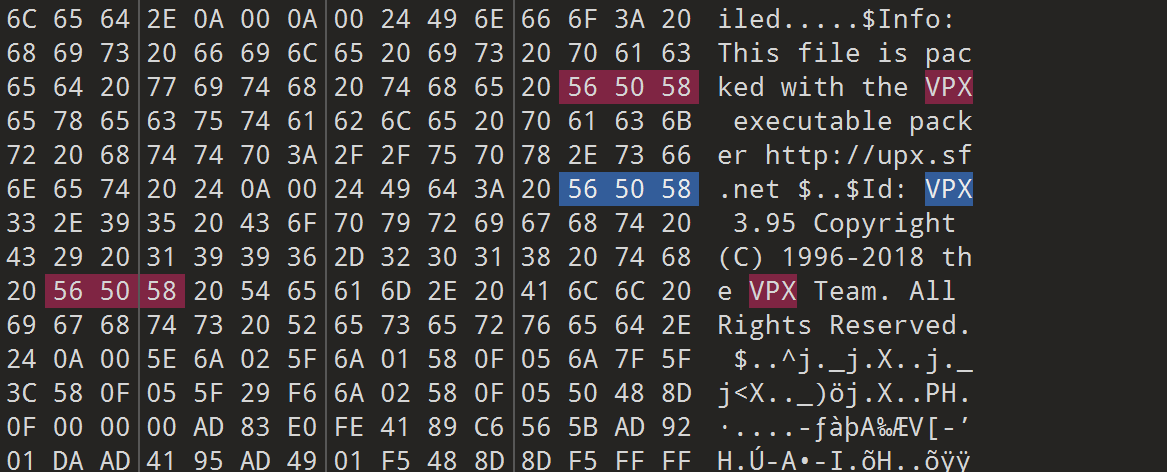
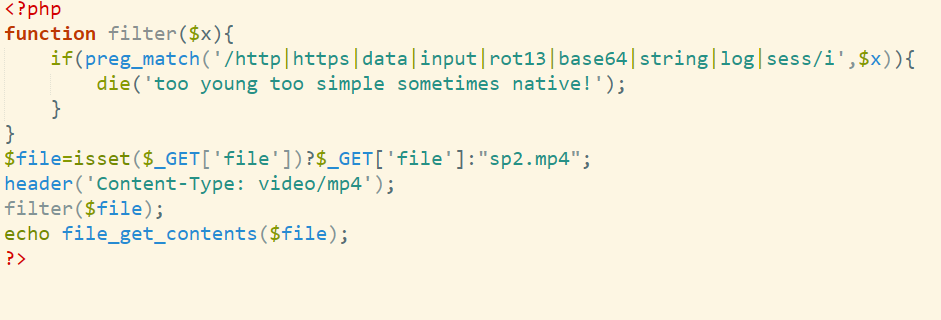
upx_revenge
全部改回UPX
控制流平坦化
D810实测无法去
试试angr大法
也不太行
动调是唯一出路
tsctf-j_2022/writeup.md at main · MakeMerakGreatAgain/tsctf-j_2022
做不出来,好难…